The Cyber Investigator CTF created by Jack Tilsen of Cyber Society at Cardiff University is OSINT themed and can be played here: https://investigator.cybersoc.wales/
I have not included files given alongside the challenges in this write-up, so to fully understand the write-up, you have to open the challenges yourself.
Signals Intelligence
foreigntransmission
Our signals intelligence team has captured a transmission originating from Western China and we have reason to believe that it may provide us with some kind of code that might be meant for a field operative of theirs. We’d like to know what it is.
The translation team is not available for us to utilise at the moment, so I’m wondering if you can use any of your digital tricks to work out what the code in the recording I’ve attached is?
Expected flag format: ###############
https://investigator.cybersoc.wales/challenges#foreigntransmission-23
I googled for an “audio translator” first, but generally speaking, going for “automatic subtitles” first and then translating the Chinese output separately would be smarter. I used this website for automatic subtitles: https://www.veed.io/
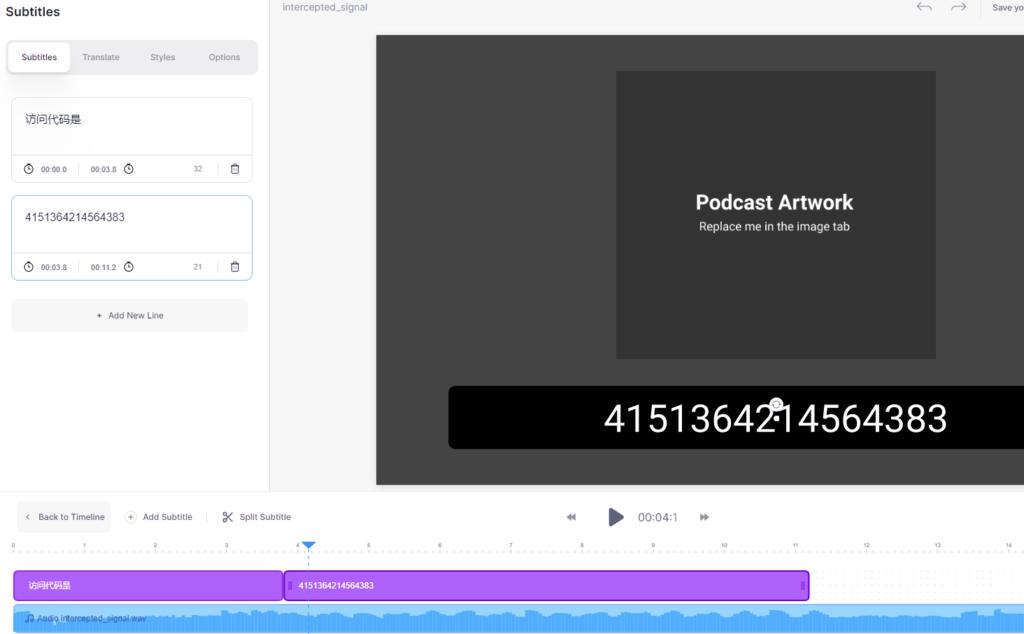
The result was 4151364214564383, which didn’t work. When I compared the number of digits with the expected flag format, I realized, that the automatic subtitles generated one digit extra, so I had to listen to the audio a few times to make out which digit was not actually spoken.
Answer: 415364214564383
personalbanker
We’ve been granted authorisation for a wiretap on a phone belonging to a kidnapping victim; no calls have been made since they disappeared however just recently, there was a call made to a bank where the caller inputted a debit card number.
Can you find out the 16 digit card number so that we can trace the spending activity associated with this card? This will be very helpful in our effort to locate who may be a potential suspect in this case.
Expected flag format: ################
https://investigator.cybersoc.wales/challenges#personalbanker-18
I was actually confronted with this kind of riddle before. The dial tones you hear are called DTMF and there are various tools to decode them. I used this one: https://unframework.github.io/dtmf-detect/#/grid
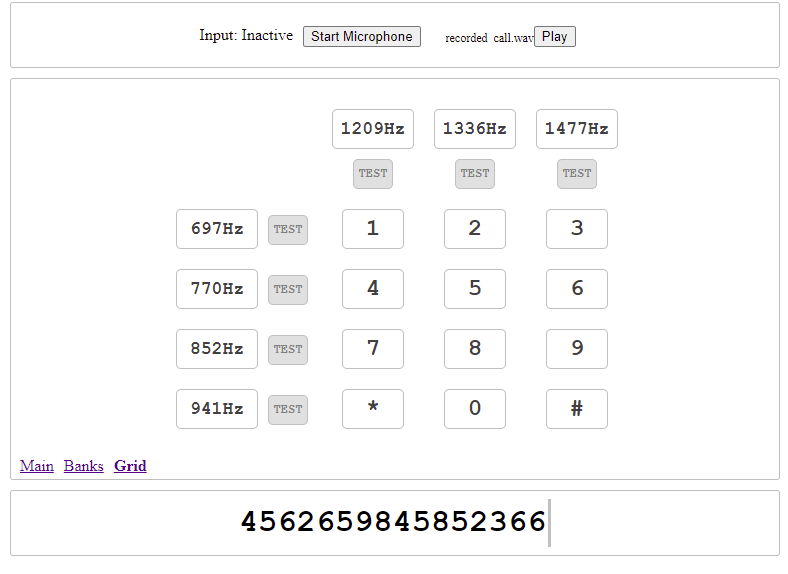
Answer: 4562659845852366
faultycassette
As part of an investigation into an individual we believe is responsible for a slew of email threats directed at senior politicians, we have been digging up boxes of evidence from various forests around the UK.
From a few feet beneath Grizedale forest, we’ve recovered a cassette tape that when played, has what sounds like some unrecognisable speech. We don’t know who it is or what they’re saying.
It isn’t clear what the suspect was doing with this, or whether they intended for us to find it.
Are you able to identify who is in the recording for us? I’ve attached a digital copy of the tape.
Note: you’ve only got 3 attempts so refrain from just guessing!
Expected flag format: firstName(space)lastName
https://investigator.cybersoc.wales/challenges#faultycassette-24
When I listened to the audio for the first time, I immediately realized it was played backward. So I put it into Audacity and reversed it.
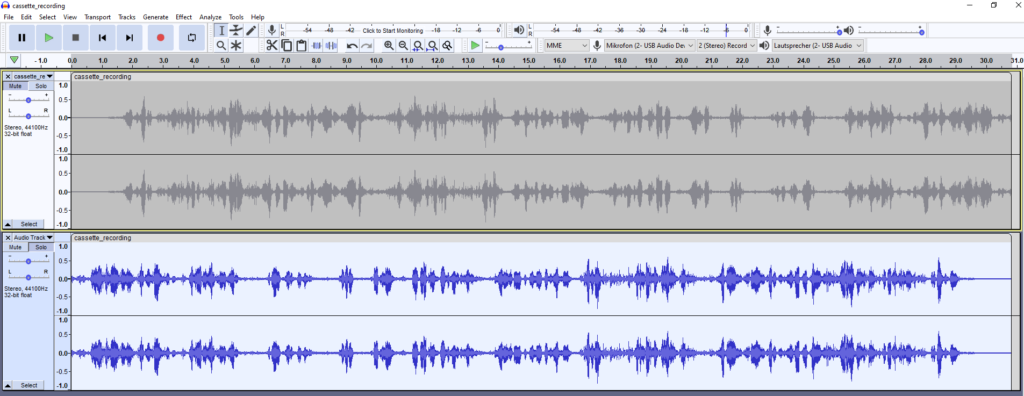
Then I just had to transcribe some of the text and google it: “When I walked in there, there were 18,000 people waiting over a year for their operation. Today it’s just 800. Too many. Still too long.”
It’s David Cameron’s farewell speech from 2016.
Answer: David Cameron
armageddon
Uh oh… tell me where it’s headed so we can let them know it’s over.
Note: You have only 3 attempts for this one.
Expected flag format: nameOfTarget
https://investigator.cybersoc.wales/challenges#armageddon-42
This one was the last challenge of the Signals Intelligence category and had the highest points out of all of the challenges. I assumed it had something to do with sound, because that was true for the previous challenges, too. So my first thought was that the image showed some kind of sound, maybe a spectrum or volume. Before thinking too much about it, I tried reverse image searching for the image as well as extracting EXIF data, but none of them worked.
So I just googled “sound image spectrum to audio” and tried this result: https://nsspot.herokuapp.com/imagetoaudio/, but that didn’t work. Next, I tried https://melobytes.com/en/app/spectrogram, but that didn’t work either. I then tried a more generic approach with https://melobytes.com/en/app/image2music, which just converts an image into music. The result was actually music. Shazam thought it was “Colors” by “Nosite | T”, which was similar, but not quite, and I didn’t know how to proceed from there, since I needed some kind of direction as the answer.
Interestingly, it seems to be quite common to play with images and sounds, so there are many tools and methods to convert one into the other. I tried many of them. Finally, what worked was a tool called Photosounder (https://photosounder.com/download.php).
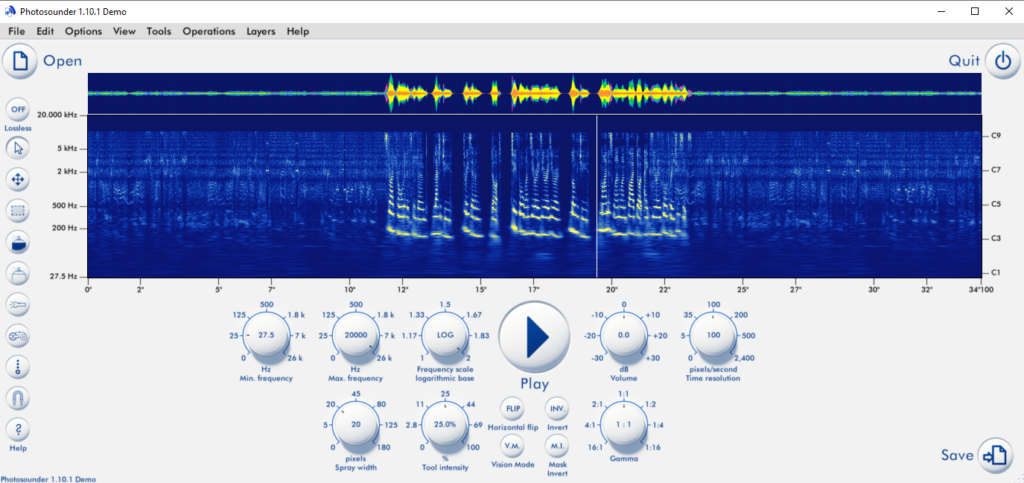
A voice says a couple of numbers after stating “latitude” and “longitude” before them. So those numbers are obviously coordinates of some place: 37.241000 -115.804326. Googling those coordinates reveals the place is “Area 51, Nevada, USA”.
Answer: Area 51
Covert Operations
thermalentry
One of our undercover officers has been following a suspected financial crime kingpin and they keep visiting a lockup in a secluded area of London – we have no idea what is in there.
A couple of nights ago, the officer noticed that there is a digital PIN pad used to open the lockup door, and shortly after the suspect entered and closed the door behind them, our officer promtly approached the PIN pad and took a photograph of the keys with a thermal camera.
Research into the PIN pad reveals that it only accepts four digit codes, so that should make things easier.
What is the PIN code for the lockup? It will be much easier for us to make a subdued entry to find out what is in there without compromising our investigation through forcing our way in.
Note: You only have 5 attempts so inspect the image very carefully before checking your answer.
Expected flag format: ####
https://investigator.cybersoc.wales/challenges#thermalentry-26
This challenge gave the least amount of points out of all challenges. We are looking for four digits and we can see four red dots on the keypad. Logically, the more red we can see, the more recently the pad was touched. The last two are difficult to order, but with 5 attempts, that’s doable.
Answer: 4158
nightclub
We’ve been monitoring the movements of a few somewhat well-known club DJs-for-hire with sketchy pasts.
A couple of days ago, we parked one of our investigators outside a nightclub which previous checks suggest is linked to a drug-related money laundering scheme. We also happen to know that each of the DJs we’ve been following use Spotify for their music at venues.
Unfortunately, the DJ for the evening must have used another entrance as our suveillance team didn’t spot anyone matching the profile of any of our suspects that night.
It would be useful for us to know the name of the song that is playing in the attached recording, as this will enable us to scrape the listening histories of our suspects and match the two up to identify who was there at the time.
We’re hoping to recruit this particular DJ and leverage the likely trust that has been established with the club management to utilise them as an informant.
This will help us to infiltrate the drug gang running the nightclub and move us closer to dismantling their operation.
Expected flag format: XXXXXXXXX
https://investigator.cybersoc.wales/challenges#nightclub-19
I don’t know if this can really be called a challenge, since there is an app called “Shazam” that can tell a song by hearing it: https://www.shazam.com/
Just open the app, play the audio file for a couple of seconds, and get the answer.
Answer: Limitless
orientalnavigator
We recently performed a search of a Yacht parked in a berth in Hawaii; fairly strangely, a lookup of the vessel’s paperwork yields no results and we don’t have time to draft in someone with enough knowledge of boats to be able to provide us with further context.
However, we did find what looks to be a dash cam with footage of someone driving through what we suspect is a town or city in Asia.
I’ve attached an image showing a road sign from one of the clips found on the camera, could you take a look and see if you can work out where the driver was at the time?
Note: You only have three attempts for this, so make sure you don’t just guess!
Expected flag format: townOrCityName
https://investigator.cybersoc.wales/challenges#orientalnavigator-22
I used Yandex’s OCR (Optical Character Recognition) for this challenge: https://translate.yandex.com/ocr
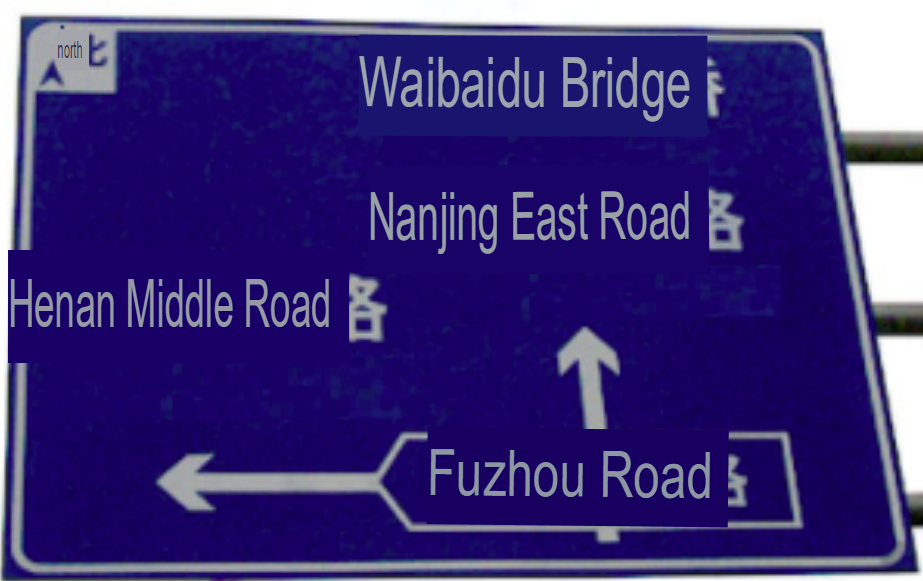
I then googled the street names to possibly find a crossroad or something, but I quickly realized the city is Shanghai, so it doesn’t have to be more precise than that.
Answer: Shanghai
telemanipulation
We believe we’ve found an address where a number of victims of human trafficking are being held. We know that there are anywhere between 1 and 3 grunts posted to guard the premises at any given time, but in the early hours of the morning, they seem to watch TV most of the time.
I have been thinking about a distraction technique to get them all into the living room at the same time whilst we make quiet entry into the property before hurling a flashbang into the lounge and getting the drop on them, hopefully without firing a shot so we can keep them in a fit state to tell us all about the intricate workings of their organisation.
A way of getting them together to deliberate might be to cause a problem with their TV.
Our guys sat on the hill not far away and spotted the below remote control in one of their hands, together with a TV as pictured on the unit in the lounge.
I know that these remotes are programmable, could you find out the code to set the remote to control this brand of TV?
This will enable us to switch off the TV, fiddle with the sound, change inputs and so on – hopefully causing a stir long enough to distract them.
Note: You only have 4 attempts here, so make sure you do your research!
Expected flag format: ####
https://investigator.cybersoc.wales/challenges#telemanipulation-31
I used Google Lens to search for the remote control and found out it’s a “SKY Q Voice Bluetooth Version 2020”. The TV is a Toshiba as indicated by the branding on the top left of the frame. Then I just had to find the correct code for this TV and the remote, so I googled “sky tv remote code” and found this page: https://sky.uebv.com/
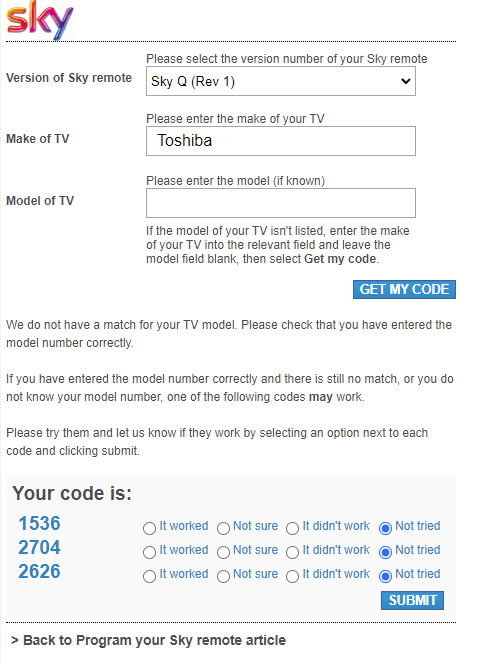
I didn’t know the exact model, so I just wanted to try all three codes, but the first one worked.
Answer: 1536
armsdealer
We’ve been tracking a cell on the horn of Africa and one particular target has fallen under suspicion. Our agent deployed there has found out that the target always stores his handgun in a small compartment of the boot of his car, which following some research on this particular model of the car, measures in at 200mm x 135mm (length x width).
Our agent believes that they have recovered the target’s weapon but to help confirm this, we need to establish whether it ties in with our theory about putting it in the boot. We have no idea what the gun is, so could you use your talents to find out the length and height of the handgun pictured?
By the way, the agent said that some parts of the handgun feel rough – like sandpaper – perhaps a brand name has been sanded off somewhere along the line.
Note: You have just 5 attempts so again do not just guess!
Expected flag format (length first): ###mm x ###mm
https://investigator.cybersoc.wales/challenges#armsdealer-41
I googled ["19 austria" "9x19”] to find out it’s a “Glock 19 Austria 9×19”. I then googled that to find out there are multiple generations of it. Judging by the images, the one we are searching for is “Gen 3”, so I googled “glock 19 austria 9x19 gen 3” which led me to this page: https://www.arms24.com/glock-19-gen3-pistole, which lists details of the weapon: Length: 18,7 cm, Height: 12,8 cm.
Answer: 187mm x 128mm
disembark
I’ve been anonymously emailed some footage with a siren blaring in the background and a scene of chaos and panic, with people running out of open spaces seeking cover. I’m not quite sure what to make of this.
Could you take a look at the clip for me and let me know the name of the country in which it was filmed?
Will be a big help and a good start to building up a picture of what its all about.
Note: You have just 5 attempts for this so keep a sharp eye out.
Expected flag format: nameOfCountry
https://investigator.cybersoc.wales/challenges#disembark-39
The video was branded by RT (Russia Today), so it was probably not filmed in Russia. Things to look out for when trying to figure out a city are things like landmarks, street signs, license plates, and advertisements showing phone numbers and web domains.
At one point in the video, a minibus can be seen:

Googling “mashdan.co.il” reveals it is from Israel, but that doesn’t have to mean the scene is in Israel.
Additionally, a building is shown:

Google lens tells us this could be the Servcorp Diplomatic Commercial Office Tower in Manama, Bahrain, or it could be the Moshe Aviv Tower in Tel Aviv, Israel. Since two hints point towards Israel, that was my first guess, which was correct.
Answer: Israel
aviator
We’ve dug out a memory stick from a safety deposit box on the east coast of the US after following up on some leads over there, but all of the modified/access/creation timestamps have been wiped, meaning that we don’t have even the slightest idea of when it was last used.
Said memory stick contains an array of incriminating files which prompt us to want to speak to whoever the memory stick belongs to.
Amongst the files on the drive, we have found a recording of a Boeing 737-800 aircraft taking off from some airport.
Can you find the latest possible date that the video was taken? This will help us to gain a ballpark idea of the age of the rest of the content on the seized memory stick. Note that the metadata of the video file itself won’t be any use in this case.
Attempts are capped at 5, so refrain from completely guessing!
Expected flag format: DD/MM/YYYY
https://investigator.cybersoc.wales/challenges#aviator-20
This one took me quite some time. In the clip we can see a country flag:

That could be Columbia, Venezuela, or maybe Armenia. We can also see an aircraft with the text “Laser”, which is hard to google on its own unless you google specifically for an “airline” called “Laser”, which I assumed was the meaning of the text:

That’s an airline from Venezuela. More specifically, from Caracas.
Now the idea was to find out when the last Boeing 737-800 from American Airlines departed from the airport in Caracas towards the “east coast of the US”. According to some sources, “American Airlines ground[ed] 14 planes due to overhead bin issue” (https://www.reuters.com/article/us-american-airlines-maintenance/american-airlines-grounds-14-planes-due-to-overhead-bin-issue-idINKCN1QO2IP). So it seemed some of the last airplanes departed on 25/01/2019. Another source (https://www.alamy.com/an-american-airlines-boeing-737-800-airplane-takes-off-at-simon-bolivar-international-airport-in-caracas-venezuela-january-25-2019-reutersandres-martinez-casares-image372523249.html) shows a take-off on the same date. Maybe because it is an important date because it is the last on which the Boeing 737-800 could take off? Unfortunately, that’s incorrect.
So I searched “day American Airlines stopped flights from Caracas” and found this article: https://www.mercurynews.com/2019/03/15/american-airlines-suspends-service-to-venezuela/#:~:text=PUBLISHED%3A March 15%2C 2019 at,2019 at 5%3A30 a.m.&text=Laya | Bloomberg News-,American Airlines Group suspended its service to Venezuela on security,by a major U.S. carrier. That was published on 15/03/2019, which is also the last day a Boing 737-800 departed there.
Answer: 15/03/2019
Cyber Crime
mysterymachine
We keep detecting an unknown device on our network in the office and records are showing that it’s connecting via one of our WiFi access points. We’d like to learn a bit more about what is going on here.
The MAC address is: 00:0a:95:10:e2:1b.
Could you tell us the manufacturer of the device that we are looking for?
Note: You only have 3 attempts so refrain from guessing!
Expected flag format: nameOfManufacturer
https://investigator.cybersoc.wales/challenges#mysterymachine-32
Just google “MAC address lookup” to get to this page: https://www.macvendorlookup.com/ Then past in the provided MAC address.
Answer: Apple
mulemobile
We’ve sent a couple of officers to Birmingham Airport (BHX) security to help fill a temporary staffing shortage and whilst there, they have identified a male who is yielding strong readings for a presence of cocaine. He has come from Lima via Istanbul.
There seems to be a white powdery substance synonymous with this drug leaking out of the phone in trace amounts, but attempts to open the phone have failed. It seems that some sort of very strong adhesive has been used to bind the chassis togehter.
We’ve weighed the device and right now it is showing as 300g. There are no signs of life and the device does not respond when a compatable charger is plugged in. We suspect the device may have been gutted and stuffed with cocaine.
Is there any way you could find out the difference between the current weight and the original (expected) weight of the device? A substantial difference will help us confirm our hunch that the device being used to conceal a controlled substance and we’ll confidently drill into it.
Here’s a note with the details anyway…
Expected flag format: XXXg
https://investigator.cybersoc.wales/challenges#mulemobile-38
Just google “imei lookup” to get to this page: https://www.imei.info/ Type in the provided IMEI (352602081794916). It’s a “J210F Galaxy J2 (2016) (SM-J210F)” and weighs 138 g originally. 300 – 138 = 162.
Answer: 162g
databreach
Did you know about 30,000 websites are hacked daily?
We recently set up a unit alongside our counterparts in North America that is designed to actively monitor potential attack surfaces of high net worth and other high profile parties; think C-level employees of companies, those in powerful government positions and so on.
Interesting one for you… I’m trying to work out whether Elon Musk’s email address has ever been included in these huge data breaches which tend to arise from organisations’ databases/sources being left exposed to the public or attacked by black hat hackers.
The typical result of the above is that lots of personal information such as names, usernames, email addresses, passwords, physical addresses, credit card information et al gets flooded onto the dark net, where it is then used for all sorts of nefarious purposes.
Can you find out the name of the company whose data breach Elon’s email was spotted in? Here’s his outlandish business card.
Expected flag formal: nameOfCompany
https://investigator.cybersoc.wales/challenges#databreach-40
I immediately went to https://haveibeenpwned.com and typed in the email address (elon.musk@gmail.com).
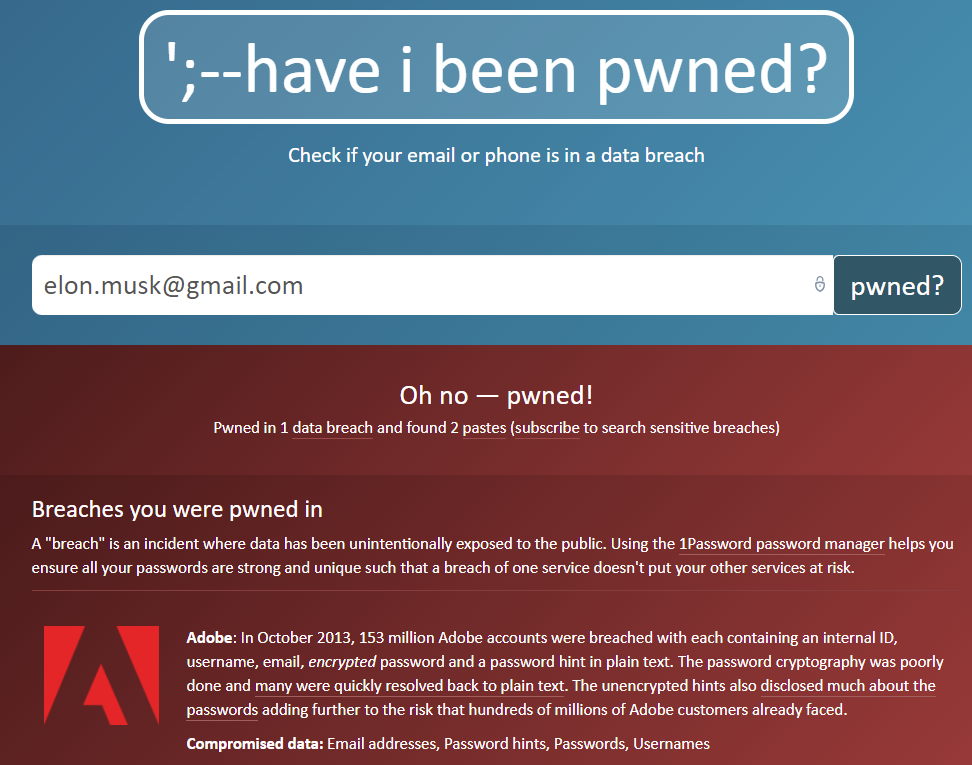
Answer: Adobe
stencil
It’s me again. We’ve been scraping the contents of some open cloud storage buckets belonging to some dark net e-commerce websites known for selling drugs, weapons, stolen credentials and so on.
I have spotted a few documents using this peculiar font, seemingly discussing the drop-off of goods (attached here).
My thinking is that it would be easier to filter out the millions of documents that we have seized if we know the name of the font used in the exemplar document, as we could then use computer vision techniques to match the full character set of said font to any of the other documents in the masses of data which use the same one, potentially finding other associated messages and detail that we may otherwise never have time to dig up.
Let me know?
Note: You have only 5 attempts for this one, so make sure you’re certain of the font.
Expected flag format: XXXXXXXXX
https://investigator.cybersoc.wales/challenges#stencil-30
Just google “font lookup” to find various websites like WhatTheFont, WhatFontIs, or FontSquirrel. WhatFontIs worked for me.
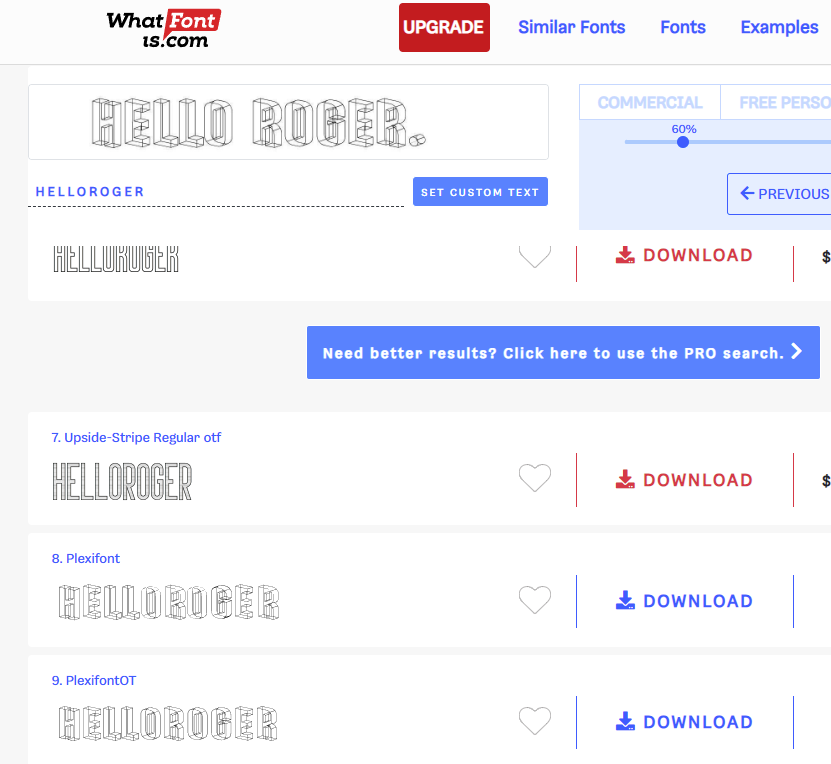
Answer: Plexifont
unmonitored
Last week, we seized a computer belonging to somebody who we believe to be involved in the logistics of a criminal organisation. Upon inspecting the contents of the hard disk in the machine, we’ve found some code held in TXT files; the person in question seems to be something of a gamer with a preference for older titles.
Attached is a sample of one of the code files we found. We’re aware of instances where similar parties contact one another using the likes of Call of Duty as the servers are not monitored; perhaps they’re using some other game in this instance to achieve the same? If it’s any help, every single one of their computer games seems to be rated PEGI 18+.
It looks like this code is some sort of tutorial, they were possibly trying to learn the language…
Could you find out the name of the video game that the scripting language shown in the attached text file is used with? This will help us to potentially narrow down who else they have been speaking to by checking for the presence of the game on other seized machines.
NOTE: Remember, its a multiplayer game.
Note: You have just 10 attempts for this so don’t guess!
Expected flag format: nameOfGame
https://investigator.cybersoc.wales/challenges#unmonitored-46
This one was a bit tricky, even though it didn’t seem like it at first. I immediately googled “AMX Native Error 4 - AMX_ERR_BOUNDS” from the text file and got to this page: https://www.amxmod.net/forum/showthread.php?tid=1167 So this code seems to be used for a mod written in a Half-Life scripting engine, or in a scripting language called “Pawn” (https://wiki.alliedmods.net/Pawn_Tutorial). The mod is used for “Half-Life”, but neither that nor “Half-Life 1” nor “HalfLife” is correct. Considering I only had 10 attempts, I assumed “Half-Life” was not the game I was looking for and instead looked for other games that use the same scripting language for mods, Pawn, which would result in having the same code snippet, but being less popular. I specifically searched for a mod that enabled multiplayer, since that’s what the provided snippet seems to do, and the text kind of hints at that. So I googled “pawn script multiplayer” and found “Grand Theft Auto: San Andreas Multiplayer” as one of the most prominent results.
Answer: Grand Theft Auto: San Andreas Multiplayer
nationstate
As part of our counter intelligence work, we have been monitoring the internet communications of a range of countries across the globe.
We recently detected some suspicious traffic hitting one of our honeypot servers (purposely set up to draw in attacks).
We have intel to suggest that certain nation states are utilising bots and other automated methods to scan resources across the internet in an attempt to retrieve files that have inadvertendly been left open to the world on web servers. This is just one of the approaches that we believe forms a part of a more comprehensive set of offensive cyber capabilities.
It looks like somebody has been looking for something quite specific in this case.
I’ve attached a text file which represents a section of the log data for this honeypot server, I’m wondering whether you could tell us which country is responsible for the traffic and which country is the likely target?
Attempts are capped at 7, so refrain from completely guessing!
Expected flag format: sourceCountry(Space)targetCountry
https://investigator.cybersoc.wales/challenges#nationstate-21
The first part is quite easy: Just google “IP to geolocation” and go to this page: https://geoip.com/ Paste in any of the given IP addresses of the log file, which shows that North Korea is the source. For the target I thought I would have to find the owner of these logs, so I tried to find them by the time setting of +0300, but UTC+3 is too broad to give any single country.
Then I decoded some of the requested URLs that all look like this: “%u0412%u043B%u0430%u0434%u0438%u043C%u0438%u0440%20%u041F%u0443%u0442%u0438%u043D”, which is Unicode and decodes to “Владимир Путин”, which translates to “Vladimir Putin”. So the target is likely Russia.
Answer: northkorea russia
stolenidentity
We found a really old USB stick in a wallet belonging to somebody we know is involved in cloning and forging passports and selling them for a tidy profit.
I’ve had a look at it myself but can’t see anything specifically incriminating, although there are a couple of photos of the covers of foreign passports stored – but this doesn’t really tell us much beyond what we already know.
The forensics guys have made an ‘image’ of the drive but they haven’t got around to looking at this yet as they are stacked with higher priority cases. I’ve attached that for you.
Can you tell me the full name on anyone’s passport you find on this drive image? We’ll need to know so that we can alert them to check their credit history for anything suspicious and perform some checks on the usage activity related to the passport to see whether its already been cloned before and has been used nefariously.
Note: You have 10 attempts for this, avoid guessing at random!
Expected flag format: fullNameOfPassportHolder
https://investigator.cybersoc.wales/challenges#stolenidentity-47
For these kinds of analyses of .dd files, I usually use Autopsy (https://www.autopsy.com/), but there are other tools, too.
Opening the image file reveals the USB drive belonged to someone called “Tyler”, but that’s not what is asked. Snooping around a bit, I found a couple of images on the system.
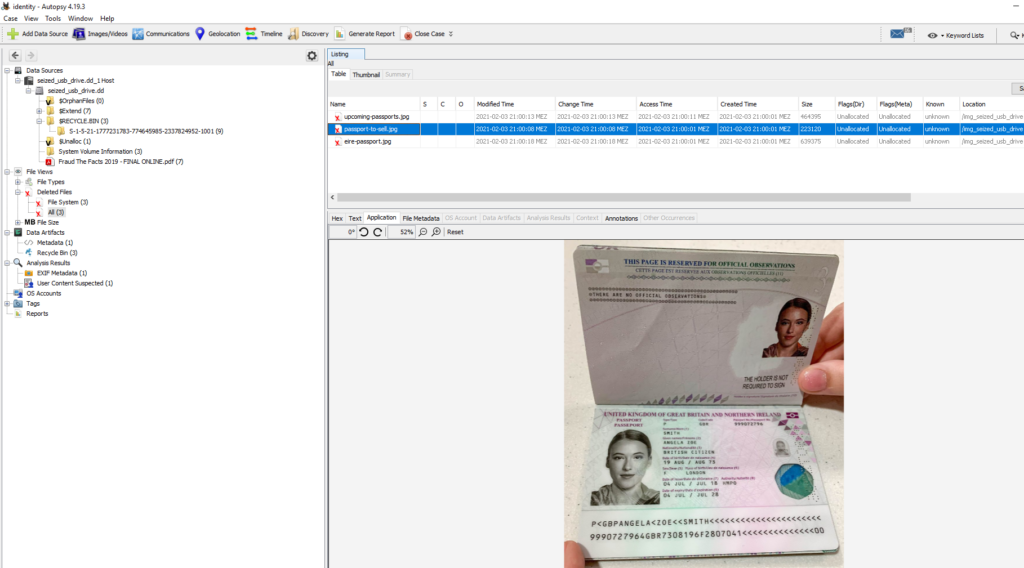
This one belongs to “Angela Zoe Smith”.
Answer: Angela Zoe Smith
remoteaccess
We recently compromised one of the SMB shares connected to a criminal organisation’s network, and would you believe we have found some SSH keys on there; I thought I’d give you one of them to have a go at cracking.
I’ve attached the private key file below for you, could you let us know the passphrase tied to the key?
If you’re not sure where to start, get Googling! You might be able to do this (reasonably) quickly.
If you can get this for us, we might be able to compromise another one of their servers by connecting right to it via SSH!
Note: You’ve got 5 attempts at this so be confident you’ve found the passphrase before inputting your answer!
Expected flag format: sshKeyPassphrase
https://investigator.cybersoc.wales/challenges#remoteaccess-48
For hash extracting and cracking, I usually use John the Ripper (https://www.openwall.com/john/). If you’re having trouble extracting the hash from the key, there are online sites for that, too, like this one: https://www.onlinehashcrack.com/tools-private-key-ssh-rsa-dsa-openssh-hash-extractor.php
The hash: $sshng$1$16$6FDAB0A1EC37A03D7B377036711AF0C7$1200$d78284beca2a7a991051646508fc66c00d7f4e9f10b20901d72ce50cd1139aa24dd4f03e7a6f6e3319e1c42affac54657b9a54b1a1dd7ee770d47b1e55ff414a6a2dc7c554fbef541666da91a52bb5251a037573af80ab3973221671fc8fa38bf311fcfece3288c7c78f04a1797fef6a4c08f20c0c6f89f3b17d53471656b8ea250a9dc1fda8f7f52360f40b290e80e7a8df874102a2c1a9eace4feeb66c944031c1d500b4d1986714bf8fc5bfc15784f6caec72571589f90f739a8dca8a48c9775b0fbee4c05fa7a089a6146b853a417dcc6d3377034ddf4d30e939318b69e489fbad5d403ed68ff2db64010e6c7408d476650682bdf70d1c3faa75aad5625434337a45afbbfca716c2ca2b2a312c18a348523ee7bdca9e018711359ef55fa1226468632d2936e3c0e4fb7e14ddc9600c12fa480972d196a94271db822419d7d42df8a1122b93359043fffb06fe9e2320c2de84ecdc6647f3c37adeb6d58b7b74dadc1f027b3d071db499b11d1cfc5d80d1fa4dc0631491928adce62e7083d43b2ea0b98f9f5549beb363cc1b2a2db56c15820227a45cf023f6f64c608ade344506b1010d45877d1b3efacbdf2eea7c54837703aa544b45c817cd1eaadaa590920875cf7002ebaf31b6e65eb515315c25253139b3b2fe332198ad1425ba54c5e97c0c3aad22cab5190dfccfe4d34226feb1a90938e94be1fa36b4575c45f0a645fcd294a4d0d201605cc3fe1c82ea1fc2663f7fe35e52f53a9796cea7ef1396448a1acf38de073b08f9942988c85a582918069ee51e2812b4d46d55e20f17b8e06a63170c602e985a1da83350fcd5db0adca1bf7f52b7f3061d658425aac6614f30a62cfdf95aab2a90e8b9d845930271b3ab0d5d28f5550b69c85e0ad6ee10e6aefdb8bac802605c4d48abc324cac41a6875f521b72d7f6b4ab398901b5954bdb1c605ac5ca6aad46e511c1f143f7a44e77fe377b5553b9cbd8dbd76271f7962444dff83c66dab1defc8df39809aef19b02e938aa3f2f786ec23fdd8449b3f54ff15fb4993576f9b569633ca72f0b17825e2c3962a03ce634ee167a752cafa17cd346de339fb37af293ec96394c1c02f42c47867f96e4bb5908d3a9a440d63fdde193226d3a52b20dc2574919fd07658736dfa6854f6e4cc1f1c22ded0e39dfa6c0b8cdac6965dc6c251b6bd54a0865b2c52e3aa7ff7744b957ad5ad468ac5f79679f9df1339116fb988a9bf78e655b88c054dc3d69e5f5aa80a631dedbf83fd08a2d6374dca0570d4ef2b79d2817dd0c4e27743dde019d9fa9a06a7f0f94e3d3d81178c27e91ea6968e02e753677297541670a8e5c791bf47767e7ef8a88f685143eaf123c823816f4519f76585a34d97e3c95394ced555d2fc7d3e99482e3f2b1d6204714d3f65894b1f3c4f41dbc28368ab23ca95cca8f9d6475472f1709e958867fcd62de94fe4f1f69368348971509b67fe464d9dd40cbf8e7deb0b06dd0c2c0cf4c2d3c1c50a3bbed041883e5cdc07d4e00189c607b670bde7227590b5188af7a64a3619a24190603cd53a5e219a5f7b0669508232d6df3299ac27b7b8be4953786b3b538752ac28ab1b5a9d74c435f8c2bdd76d1b312b946a5e854831ad701df10ac5be903c0ae74fc804c27ad721b00a238cadaf8f4bb271af900fa9b745798c3e3e3e182ded45f9e92807
Then John can give us the password for that hash using the infamous rockyou wordlist.
Answer: banana
d3c0d3r
54 68 65 72 65 20 61 72 65 20 31 39 35 20 69 6e 64 65 70 65 6e 64 65 6e 74 20 73 6f 76 65 72 65 69 67 6e 20 6e 61 74 69 6f 6e 73 20 69 6e 20 74 68 65 20 77 6f 72 6c 64 2c 20 62 75 74 20 77 68 69 63 68 20 6f 6e 65 20 69 73 20 69 74 3f
01001001 01001001 00100000 00101110 00100000 01001001 01010110 00100000 01010110 01001001 01001001 00100000 01010110 01001001 01001001 01001001 00100000 01010110 01001001 00100000 01001001 00100000 01010110 00100000 00100000 00101100 00100000 00100000 01011000 01001100 01010110 00100000 00101110 00100000 01010110 01001001 00100000 01001001 01001001 00100000 01001001 00100000 01001001 00100000 01001001 01011000 00100000 01001001 01001001
Note: You have 5 attempts at this, so be confident before you check your answer!
Expected flag format: (no hints this time!)
https://investigator.cybersoc.wales/challenges#d3c0d3r-28
You could make some guesses as to what these characters are encoded as, or you can just use CyberChef (https://gchq.github.io/CyberChef/) and let it do his “magic”.
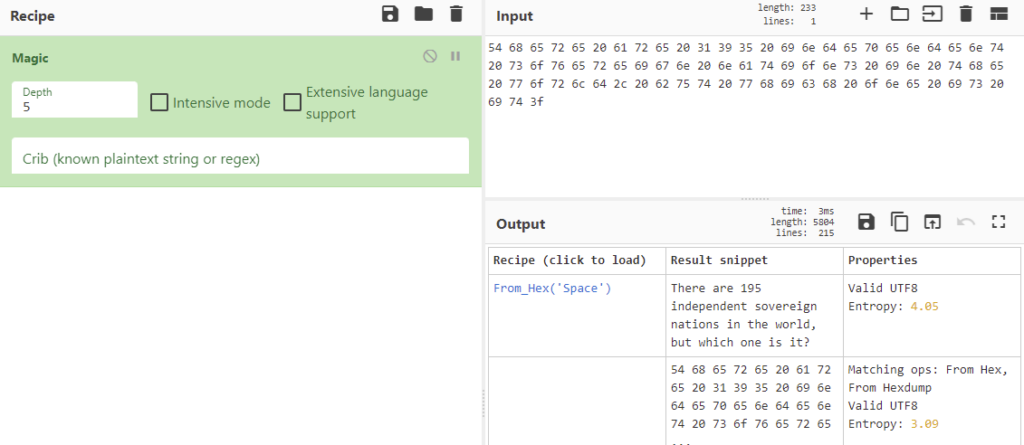
So the first part decodes to “There are 195 independent sovereign nations in the world, but which one is it?”
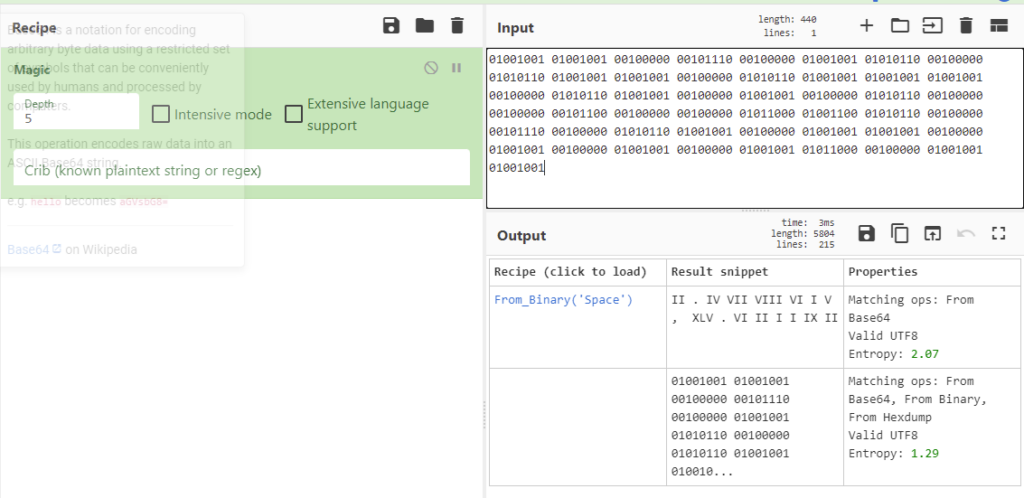
So the second part decodes to “II . IV VII VIII VI I V , XLV . VI II I I IX II”, which look like Roman numerals. Unfortunately, I don’t know a tool that translates multiple Roman numerals in one go, so I translated them manually one by one, but fortunately, they aren’t too many. The numbers are 2.4786, 45.621192. Since we’re looking for a country as hinted at in the first part, those should be coordinates. Googling them leads us to Somalia.
Answer: Somalia
Crime Scene Investigation
oink
Sometimes, criminals like to play games with us.
The other day, we forced entry to someone’s house and found something really odd smeared on the living room walls in black paint. I’ve got no clue what it could mean but we found a stuffed pig and a pen neatly placed on the kitchen table…
What does it mean?
Expected flag format: XXX XXXXX XX XXX XXXXX XXXXXXXXX
https://investigator.cybersoc.wales/challenges#oink-25
The challenge is very strongly hinting at a pigpen cipher, and the image also looks like one. I used this page to decode it: https://www.dcode.fr/pigpen-cipher
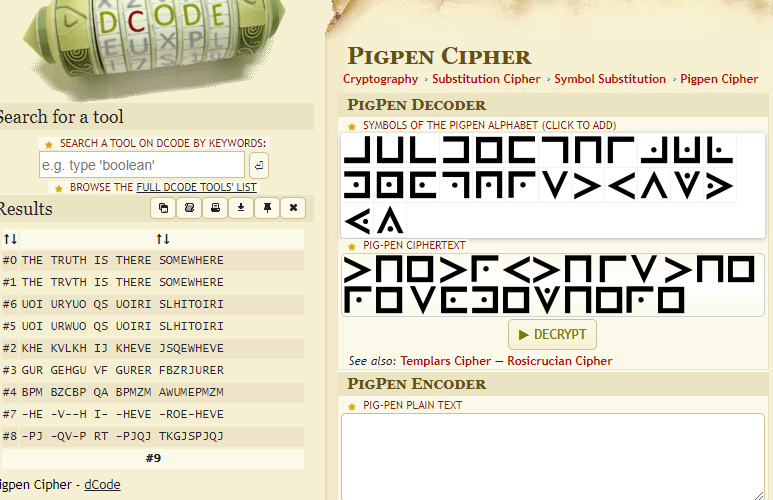
Answer: the truth is out there somewhere
spintowin
We have just attended an address linked with multiple cases of arson and upon checking the garden shed, officers found two burning candles, 4 and 5, wedged into a shelf.
They also found the message ‘Yheehp max fhgxr‘ etched into the wooden structure of the shed with what can only be presumed to be a razor blade or a knife.
Put two and two together for us; what does the message mean?
Expected flag format: XXXXXX XXX XXXXX
https://investigator.cybersoc.wales/challenges#spintowin-27
It’s a pretty short text, which can give CyberChef some trouble, but I assumed it was a Caesar Cipher or ROT cipher pretty quickly for multiple reasons: The code only includes letters, no numbers or special characters, and the flag format has the same length as the code, the title is “spintowin”, and we are given a red 45. “Red” in German is “rot”, so red numbers are very often given as a hint for a ROT cipher. I used this page to decode it: https://www.dcode.fr/rot-cipher
Answer: follow the money
gonemissing
We’ve recently been made aware of the existence of several terrabytes CCTV footage from across London that were previously presumed lost in a backup failure and have been investigating the value of this to established investigations.
I’ve been handed a cold case about a body found in a bush in Hackney, London in December 2015. I’ve not worked a missing persons’ case before but I’m told that it has a case reference number of 15-007500.
Could you find out the brand of the jacket that they were wearing at the time of their dissappearance? This will help me spot them when I’m checking the CCTV clips recorded by cameras around where they were discovered; hopefully we’ll find out how they ended up dead in the bushes!
Note: You have 5 attempts here so avoid guessing.
Expected flag format: brandOfJacket
https://investigator.cybersoc.wales/challenges#gonemissing-34
I googled “15-007500” to get to this page: https://missingpersons.police.uk/en-gb/case/15-007500. The description of the person includes “Clothing: Jacket – Anorak – Black – Plain – ‘Northface’”
Answer: Northface
restinpeace
This afternoon, some property developers made a rather morbid discovery of bones when they began digging up a plot of land to build houses on in Glasgow.
They immediately alerted us and investigators promptly attended the scene.
Alongside the remains, a Surrey County Council library card with the name ‘Ms Doris Ellen Smith’ was found together with a business card from a sewing club. This is potentially a bit odd as Surrey is over 400 miles away from Glasgow.
This, combined with the location of the bones, has prompted us to launch a murder investigation. Now, assuming that Ms Smith had links with family, friends or her sewing club, then it is likely that she was reported missing and subsequently a death certificate would have been issued owing to her not being seen again.
Could you find out the year that she was presumed dead? This will help us to establish how long the remains may have been lying there and enable us to add crucial details to our inquiries.
Note: You only have 5 attempts for this so be reasonably confident before you check your answer.
Expected flag format: ####
https://investigator.cybersoc.wales/challenges#restinpeace-33
I started by googling ["Doris Ellen Smith" "presumed dead”], but that only resulted in another write-up of this CTF and the excerpt I saw was enough to spoil it for me. However, I wanted to find it out for myself.
Searching for Surrey, England, too, brought me to this page: https://www.bucksfreepress.co.uk/announcements/deaths/deaths/19301958.Doris_Ellen_Smith__nee_Clark___Smith__nee_Clark_/ but this person has a whole website dedicated to her, which describes when the funeral took place, so that didn’t quite fit the challenge description. Also, April 2021 seemed to be a bit too late, because the earliest solves for this CTF are more than a year ago in May 2022.
The person we are looking for was also in the sewing business, but including that while googling again only leads to the write-up. So instead I tried using this page: https://www.ancestry.com/search/categories/34/ and hoped to find her there using her occupation as a filter. Since she was a “Ms” I assumed she was not married.
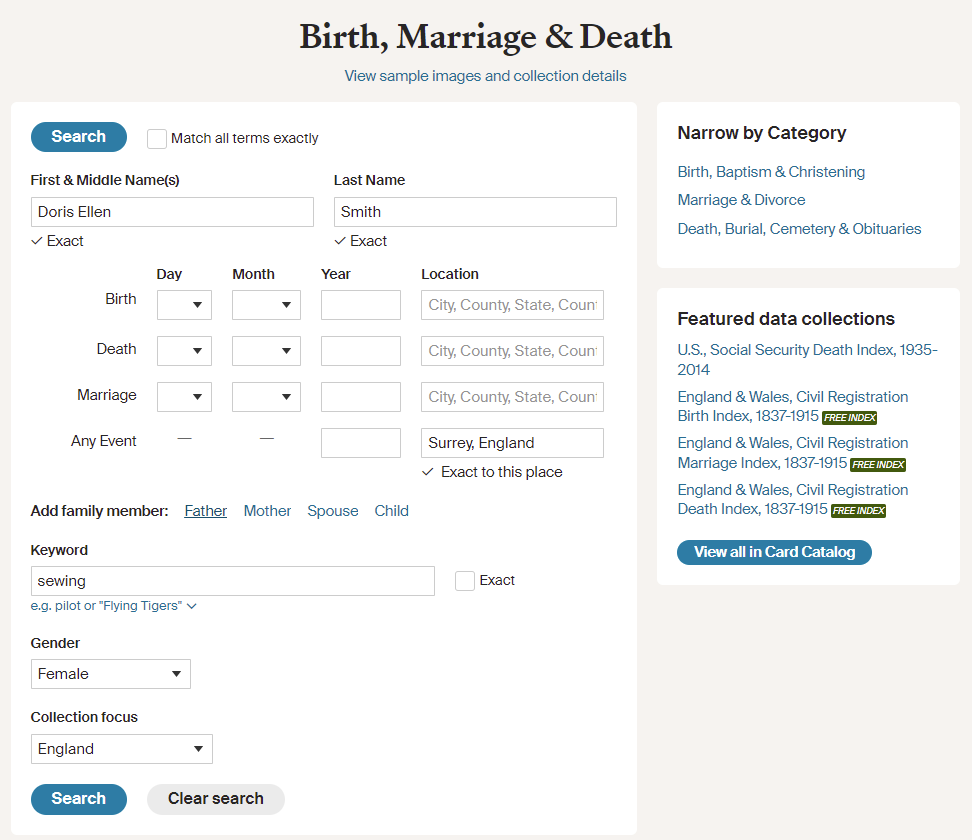
That gave 17 results, of which only one actually showed an unblurred death year. That record also stated her as “Ms” from Surrey. She apparently died in 1996.
Answer: 1996
urbanplanners
Last Thursday night, someone threw a petrol bomb at the site of an ongoing construction project at 40 Heol-Y-Deri, Rhiwbina, Cardiff, CF14 6HH. This destroyed tens of thousands of pounds worth of materials and equipment.
It is our understanding that this is an investment project whereby an old bungalow is being pulled down and replaced with two semi-detatched houses. These sorts of things can sometimes kick up a bit of a stink with the neighbours and other members of the local community, so this might be some sort of attempt to scare the property developers off.
It is necessary to apply for planning permission for these sorts of things I think, and I reckon the public are able to voice their views on proposed buildings before the decision is made by the council as to whether to approve the project and allow construction to proceed.
Perhaps there’s someone who complained? They might be a good place to start in terms of working out who committed the arson – they could either be invovled themselves or be able to fill us in on the potential motivations for this.
Could you find the full name of the person who objected to the new properties being built?
Expected flag format: XXXX XXXXXX XXXXXXX
https://investigator.cybersoc.wales/challenges#urbanplanners-35
I googled “40 Heol-Y-Deri, Rhiwbina, Cardiff, CF14 6HH” to get to this page: https://planning.org.uk/app/163/_CARDIFF_DCAPR_132839
This has limited information, but a link to the council’s website is included: https://planningonline.cardiff.gov.uk/online-applications/applicationDetails.do?activeTab=summary&keyVal=_CARDIFF_DCAPR_132839
That has exactly one public comment, which includes “With regard the above planning Application please see below my observations and objection to this development.” The comment was made by “Mary Landon Goodman”.
Answer: Mary Landon Goodman
discharged
We’re following up on an old case where a potentially key witness slipped through our grasp. Their information would have been key in cracking this case which has now gone cold.
Basically, the witness attended the accident and emergency department at a local hospital and was sat in the only seat positioned directly opposite the front desk, in clear view of a computer with direct access to the hospital’s server.
An unknown individual entered the premises and plugged something into the computer, which then automatically executed a ransomware payload but it went wrong and instantly wiped all data created over the previous 24 hours. We are yet to establish a motive or understand who is responsible. The CCTV – held off site – is too blurry to identify them from that.
We found some literature folded where they were sat, and the doctors have given us a copy of the X-ray – looks like a broken thumb. The radiologist told us that he was somewhat famous and spoke with a bit of a Scottish twang, but could not remember any more detail than that. Due to the data loss, we cannot tell who attended the hospital for treatment that day (catch 22), so the two items of evidence below are all we have to go on.
Trust me, the CCTV footage is awful – there is no way anybody would recognise even their own mother from it.
So, can you find the name of the person who was sat in that chair opposite the front desk?
Expected flag format: XXXXX XXXXXX
https://investigator.cybersoc.wales/challenges#discharged-44
Since the person is “somewhat famous” I assumed they are a politician, a sportsperson, an actor, a musician, or something like that. Considering they broke their thumb as seen in the right-hand side image (pun intended), I thought about a sportsperson, but considering they read a text from Shakespeare (Macbeth Act 5, Scene 2), they could also be an actor. Anyways, I just googled for “macbeth broken thumb” and that actually gave “James McAvoy”, who happens to be Scottish.
Answer: James McAvoy
burningrubber
We recently attended the scene of a road traffic accident where the car involved was suspected to be carrying too much weight (at top speed) and subsequently, one of the tyres blew out leading to the driver veering off the M6 motorway into a ditch – flipping over several times.
The car is a complete write-off; we’ve just barely identified the make and model of it and have found that it weighs 2200KG from checking the DVLA database.
The driver was carrying three engine blocks from a nearby scrapyard, one in the boot and two on the back seats. Each weighs 160KG.
We’re interested to know how many kilograms the car was overweight by, assuming that the driver weighs 85KG.
I’ve attached a photo of one of the tyres; all four of them are identical (including the one that blew out).
Note: You have a maximum of 10 attempts for this one, avoid completely guessing.
Expected flag format: XXXKG
https://investigator.cybersoc.wales/challenges#burningrubber-45
I started with the easy parts: The total weight is 2200 kg (car) + 85 kg (driver) + 3 * 160 kg (engines) = 2765 kg.
The tires say “205/55 R16 91V”. Google showed many sellers with product info like this page: https://www.billiger.de/products/342478066-dunlop-sport-bluresponse-205-55-r16-91v
A tire has a load index (German: Tragfähigkeitsindex), which I didn’t know before, but I just looked for anything related to weights. The load index of 91V tires is 615 kg for a single tire, so 2460 for four. 2765 – 2460 = 305.
Answer: 305KG
jigsaw
A recently-foiled terror plot has led us to raiding an address in Newcastle upon Tyne, subsequently recovering numerous weapons and a copious amount of digital evidence.
One outlying seizure that strikes me as particularly odd is a cardboard box which contained an image of someone cut out into 100 rectangles; given the history of who we are dealing with, it would be interesting to find out who it depicts.
I’ve scanned each part in no particular order but to me it is not obvious who it is. Can you find out the full name of person seen in the recovered photo fragments?
We must know if it ties in with another potential planned act.
Expected flag format: XXXXXXX XXXXXX
https://investigator.cybersoc.wales/challenges#jigsaw-37
Kindly enough, the parts were given in an archive as separate files. Unfortunately, I don’t know a website to create a jigsaw puzzle from given images, so I had to manually put them together in Gimp. Luckily, I only needed the face for a reverse search.

Google guessed it’s “primeira ministra nova zelandia” or “Jacinda Ardern”. A quick lookup of her confirmed that.
Answer: Jacinda Ardern
Financial Crime
wallstreetbets
You’ve likely heard about the recent surge of struggling brick and mortar video game retailer GameStop’s stock price, rising from a low of $2.57 to $483.00 (18,693% increase, or about 188X), madness.
It was all thanks to the collective buying power of r/WallStreetBets who managed to create a short squeeze, forcing those who bet against GME (it was a lot) to buy in order to limit losses, hurling the price even further upwards still.
We’re interested to know the name of the instutitional investor which purchased the most GameStop (GME, NYSE) shares on or before 31/12/2020. Could you find out for us?
Expected flag format: nameOfInstitution
https://investigator.cybersoc.wales/challenges#wallstreetbets-43
The financial crime challenges weren’t much fun to me and I honestly considered just not solving them, but I did anyway.
I started off by just googling “instutitional investor which purchased the most GameStop (GME, NYSE) shares on or before 31/12/2020”, which only revealed there is a lot of information, much of which is also very old. Since there is no cap on possible attempts, I just tried a few investors who had many shares of GME like “Blackrock inc” and “vanguard group inc”, but those didn’t work. After many attempts from many different sources, I ended up on this page: https://docoh.com/company/1326380/GME/institutional-ownership-history By clicking on a date in the table, they are sorted by their shares/values, with FMR being on top: https://docoh.com/company/315066/fmr-llc I tried “FMR” and “FMR CORP”, which didn’t work. A quick search revealed they are and were also called “Fidelity Investments” and “Fidelity”. “Fidelity” was the correct answer.
Answer: Fidelity
therichestdoge
I’m sure you’ve heard of Bitcoin… You’ve probably heard of Ethereum… What about Litecoin?… Stellar? There’s loads.
These are cryptocurrencies which (in a nutshell) are designed to cut out middlemen such as banks and facilitate peer to peer transactions so the only person you have to trust is yourself. The likes of Ethereum take things a step further with the idea of smart contracts, but I digress.
Anyway… There’s a coin based on the meme dog, Doge. The other currencies I mentioned have all been surging in value recently, and Doge had its moment of glory too, roaring upwards by a blistering 1000% in the space of about a day. It has since crashed spectacularly, but still seems to have momentum.
Dogecoin originally started as a joke, but hilariously people are actually making a killing from it…
We’re starting to wonder who is making the most money out of all this, so could you find out the address of the richest Dogecoin (DOGE) wallet in the world, and also state the date when the wallet first became active?
Expected flag format: walletAddress(space)YYYY-MM-DD
https://investigator.cybersoc.wales/challenges#therichestdoge-49
Naturally, the first thing I did was to google “richest Dogecoin (DOGE) wallet”, which led me to this page: https://bitinfocharts.com/de/top-100-richest-dogecoin-addresses.html
At the top, there is “DBs4WcRE7eysKwRxHNX88XZVCQ9M6QSUSz”, which I tried combined with the first transactions being on “2021-02-06 20” (Received) and “2021-04-12” (Sent), but none of these worked. So I assumed, I had to use the wallet id instead of the address. The id is “3334959”, but that didn’t work either. That’s when I assumed the answer changed over time since the wallet I found only became the richest in late 2021. The former richest address was this one: https://bitinfocharts.com/de/dogecoin/address/DH5yaieqoZN36fDVciNyRueRGvGLR3mr7L as can be seen by the huge dip in late 2021 and the little “#1” in May 2021. This in combination with the date of the first received transaction is the correct answer.
Answer: DH5yaieqoZN36fDVciNyRueRGvGLR3mr7L 2019-02-06
herdimmunity
One of the great things about modern science is that it can make almost all of our problems go away, including the Coronavirus… However, some people wish to take advantage of the situation and make ill-gotten gains.
We have discovered what we believe to be a criminal enterprise named Vaccinas International (EUROPE) which seems to be based out of France, and they have been processing numerous orders from a group of the Russian super rich.
The prices charged by this organisation are excessive and their transactions have been flagged as suspicious as a result, and my hunch is that this is a money laundering operation designed to wash dirty cash by running it through what was set up to look like a legitmate company.
Further, I’m not sure what this individual would be planning to do with millions of Covid-19 vaccine doses; whatever it is, it is unlikely to be positive… if the doses actually exist that is.
To help us strengthen this argument and to support further investigations into this firm, could you find out the percentage increase in price per dose between what the European Union paid and what the customer associated with this invoice paid for Pfizer-BioNTech vaccines?
You will need to find out what the EU paid yourself, I don’t have that information, sorry.
Note: You only have 8 attempts so refrain from blindly guessing!
Expected flag format: XXX%
https://investigator.cybersoc.wales/challenges#herdimmunity-29
Googling “European Union paid pfizer biontech” led me to believe the EU agreed on 15.50 € per dose, but since I only had 8 attempts for this challenge, I searched a bit further and found out the EU paid 19.50 €. From the invoice, we can see someone paid 84 € per dose.
84/19.5*100 = 430 or 431%, depending on how to round, but since it’s about the increase, the answer should be 330% or 331%, except it isn’t. So I also tried using 15.50 €, again having to take two guesses because I wasn’t sure how to round, but both of those were incorrect, too.
Since the text speaks of “France”, I looked up what they paid individually, but couldn’t find anything that stood out. I considered creating another account just to test 430% and 431%, too, to not just input the “increase”, but before that, I wanted to use 7 of my 8 attempts. One number I tried was accidentally leaked by Eva De Bleeker from Belgium on Twitter in a table with prices for various vaccines. The table apparently showed they paid 12 € for BioNTech.
84/12*100 = 700 → 600% increase. I think this challenge is unfair, since there is no mention of Belgium specifically, and many sources point towards 19.50 €, especially newer sources than the one from Belgium. Limiting us to 8 attempts while 15.50 € and 19.50 € both take two attempts each because you don’t know how to round the number, is tough.
Answer: 600%
And that concludes my write-up. All in all, there were many fun and diverse OSINT challenges of low to medium difficulty, and most of them were very fair.