The Downtown Murderer CTF created by Hacktoria is OSINT themed and can be played here: https://hacktoria.com/operations/operation-downtown-murderer/
The CTF was active in May of 2022.
Mission Briefing
from: julessharpe555@tiberianserpent.com
to: tmp-agnt007@tiberianserpent.com
date: May 01, 2022, 21:00 EET
subject: Briefing “The Downtown Murderer”So bit of a different task we got on our hands this time. The local Police Department has their hands full with a murderer. New cases every week, severed limbs and cut eyes and all, very horrible stuff. Due to the nature of the killings, public pressure is mounting and the city is rapidly panicking.
Your task is simple, catch the killer.
Below you’ll find the summary of the killings up until this point, the victims and timeline of events.
Good luck on this one, there’s a lot of pressure on this.
Step 1
What do all the victims have in common? Why are they being targeted?
(one word answer)Download the Police Reports Summary.
Upon opening the provided police report we can see 6 pages with similar structures: Each page contains information about a victim, including their names, gender, date of birth, a photo, the cause of death as well as a summary of how they were found.
When asked what people have in common, I usually start by checking gender and age, but quickly realized those were not the same across all victims. What I did notice, however, was that most of the victims were murdered gruesomely with a strong focus on their eyes, but not everyone was killed the same way. The way they are killed (modus operandi) is not why they were targeted, as every person can be killed the same way. Then I looked through the dates of their deaths and the locations they were found in, but apart from the same state, nothing really stood out, and considering there are many people living in each state of the USA, knowing in which one the killers operates does not give us an advantage and can be a mere coincidence because the killer might just be living there. Then I read through the summaries in hopes of finding a similar hobby or ritual, but that didn’t yield anything either.
The last thing I considered holding any information were the photos of the victims. Since the killer seemed to focus on the eyes of the victims, I did as well. It immediately jumped at me since it’s most prominent with the first victim: All of them have different colored eyes. A quick google search reveals this is called Heterochromia and it’s a pretty rare condition, so it is fair to assume it’s not just a coincidence and most likely why the murderer targeted them.
Answer: Heterochromia
Step 2
Alright not sure how you’re getting on with figuring out why these people are targeted, but we believe the killer just left us another clue. We received the follow message with 3 attached images:
“You missed a few, they deserve to rest properly”
Below are the images of the three locations, identify where these are so the local police units can look for bodies. We need the names of the locations.
Provided are three images.

Location 1 is very straightforward and can be found by simply using Google Lens and clicking on any of the sources:
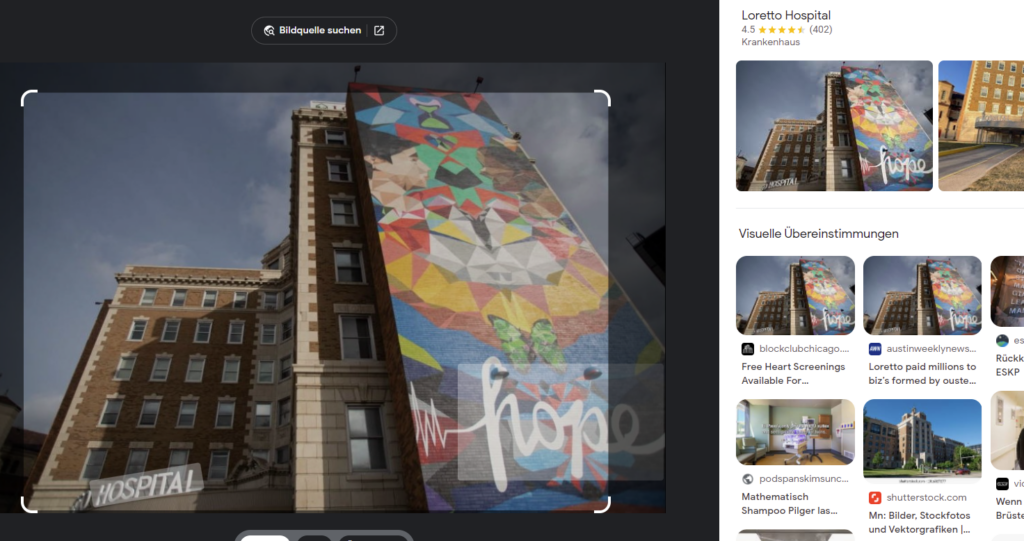
It’s the Loretto hospital in Chicago, which is fitting because the killer seems to operate in Chicago.
Location 1: Loretto Hospital in Chicago, Illinois

Location 2 was a bit more tricky because Google Lens thinks it’s a place called “brivdabas muzejs”, but looking at the windmill there reveals that it is something else. Also, that place is in a country in Europe, so that wouldn’t make sense.
After browsing through some more results of Google Lens, I switched over to Yandex and I immediately found a very promising result for the windmill.

However, that source doesn’t provide the name or location of the windmill: https://pixabay.com/photos/landscape-windmills-sky-3771522/.
But since it looked exactly like the one provided, I sent that over to Google Lens, which immediately told me what it was.
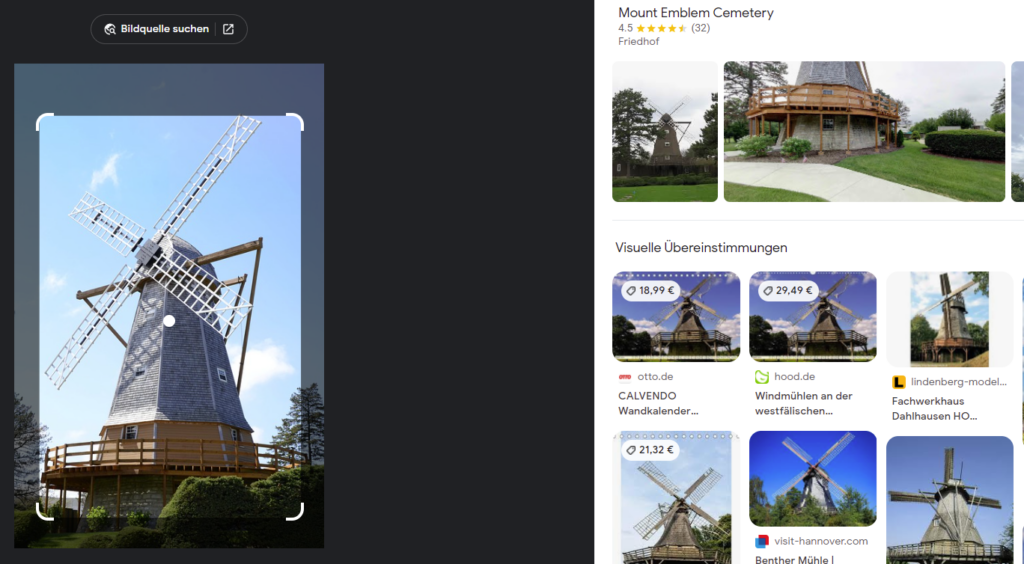
I quickly double-checked if the result was plausible by comparing more images of the Mount Emblem Cemetery to the image we are searching for.

Also, the cemetery is located in the same state as the killer.
Location 2: Mount Emblem Cemetery in Elmhurst, Illinois

Naturally, the third image was bound to be the most difficult to find. I quickly realized I would first need to figure out what the logo was on the right-hand side of the image because there are thousands of sports fields that look very similar to the one in the image. So I cropped the logo from the image and asked Google what it was.

Google wasn’t of much help again.

So I sent it to Yandex.
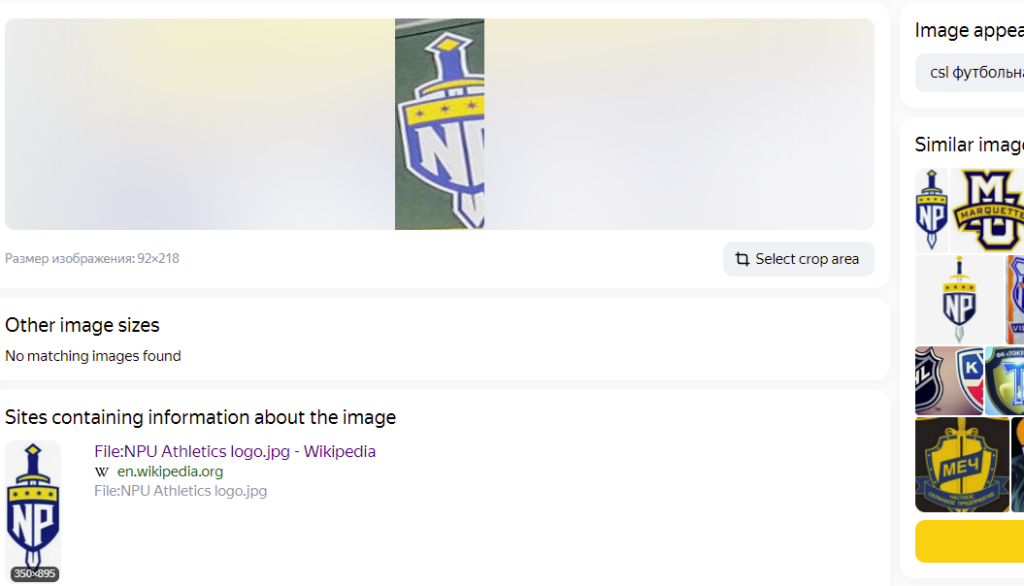
That’s more like it.
Googling “NPU athletics” reveals it’s the logo of “North Park University Athletics”. Googling “North Park University” confirms they are located in Chicago, so that’s most likely the correct track. Googling “North Park University Athletics” also shows they have some facilities for their athletes, which makes sense.
I took a closer look at their most prominent athletic complex, the Holmgren complex: https://athletics.northpark.edu/sports/2011/11/4/Holmgren%20Athletic%20Complex.aspx
Especially this image looked very promising: https://athletics.northpark.edu/common/controls/image_handler.aspx?thumb_id=13&image_path=/images/2021/9/28/183823164_10158371793309682_597734499928730419_n.jpg
Searching for other images of that complex shows this image:

Comparing the top right corner to the image we are looking for is similar enough for me. The color of the spot on the top left corner is different in different images.
Location 3: North Park University Holmgren Field in Chicago, Illinois
Step 3
Excellent work on finding the locations, the state of the victims matches the killers MO exactly. In a twist of fate, or by the hands of the killer, we’ve received an anonymous tip regarding a video that surfaced. It’s on a completely new YouTube channel, no other content posted, we believe the account to be a sock puppet.
We need you to find out the meaning of the video on this channel. Does this get us anywhere?
I started by doing the usual OSINT: Looking through the channel info, reverse searching for the profile picture, extracting the keywords associated with the video, and all that, but that didn’t reveal anything.
When watching the video, I quickly noticed the distinct sounds it played. I know from other CTFs and riddles that text can be embedded in sounds through various means, so I downloaded the video and extracted the audio for further analysis. My first instinct was to make a spectrum analysis of the sound file using this website: https://academo.org/demos/spectrum-analyzer/
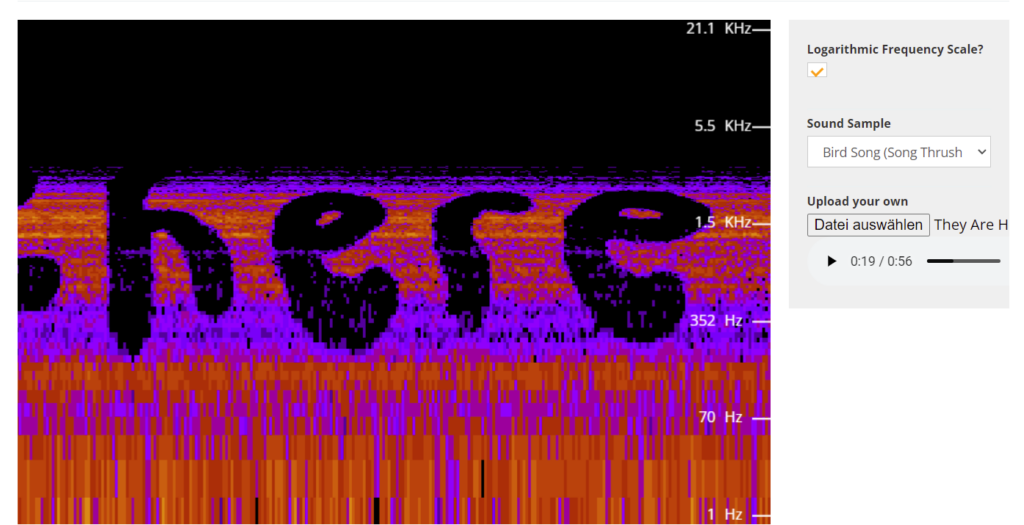
When I could read the first letters, I exclaimed, however, I did have some trouble making sense of it because I expected coordinates or the location of a place, so I had to re-read what I was presented with a few times until I finally understood what each letter meant. For example, I confused “blog” with “6109” at first.
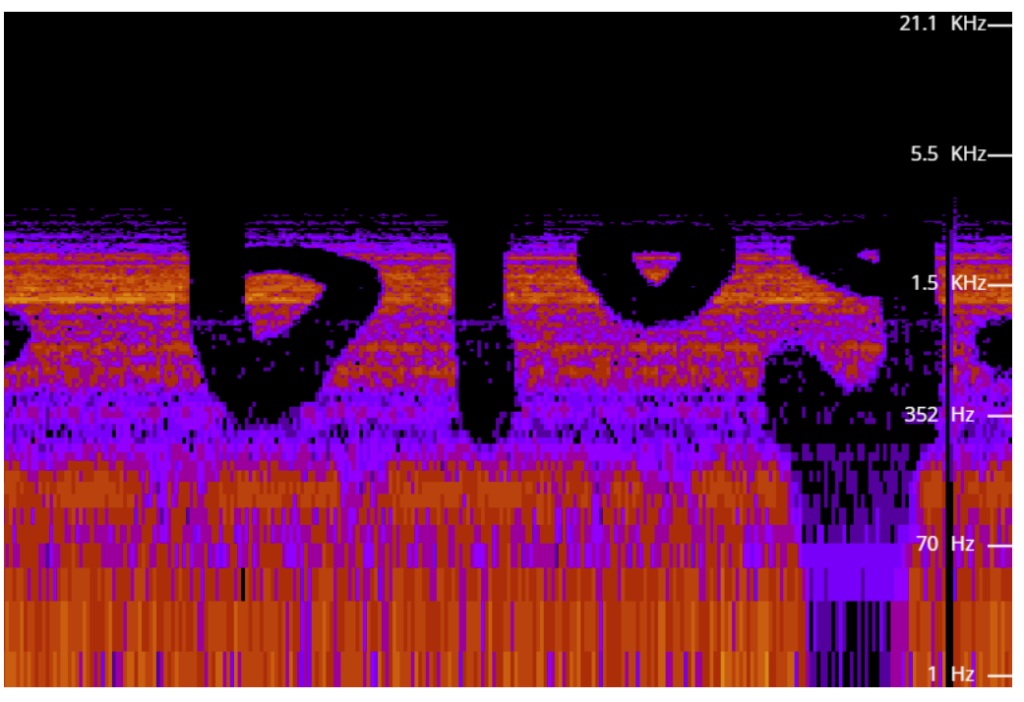
The full text says: theyarehereamongus.blogspot.com
Going there and reading through some of the articles quickly confirmed this was the blog of the murderer we are looking for.
Answer: https://theyarehereamongus.blogspot.com/
Step 4
Amazing job on finding the meaning of that message. Local PD wat chasing down a rabbit hole deep enough to come out China, excellent work. So we just got word of a new missing person, her name is Julia Morena, 35 years old from 210-200 W 4th St, Hinsdale, IL 60521.
Julia never arrived for her evening shift at the hospital two days ago, her coworkers couldn’t reach her so they contacted her family. After getting nowhere, they contacted us. Please locate Julia and find out if her disappearance is related to the killings. We will need her location, dead or alive unfortunately. I suggest you keep an eye out in case the killer posts something about this.
This one took me a while. And I would like to note that I didn’t solve step 3 before step 4 was available, and since I expected step 3 to take some technical effort (which it did), I started solving step 4 before step 3. That’s why I went full OSINT on the details given about the victim, even walking from their home address to the nearby hospital in Google Street View.
When I finally went ahead to solve step 3 first and found the blog, I knew where I had to look: The newest entries in the blog, as hinted by the step briefing.
The newest article at the time was this one: https://theyarehereamongus.blogspot.com/2022/05/i-think-i-have-something.html
Having read the other articles too, I quickly noticed the text looked completely different in this entry.
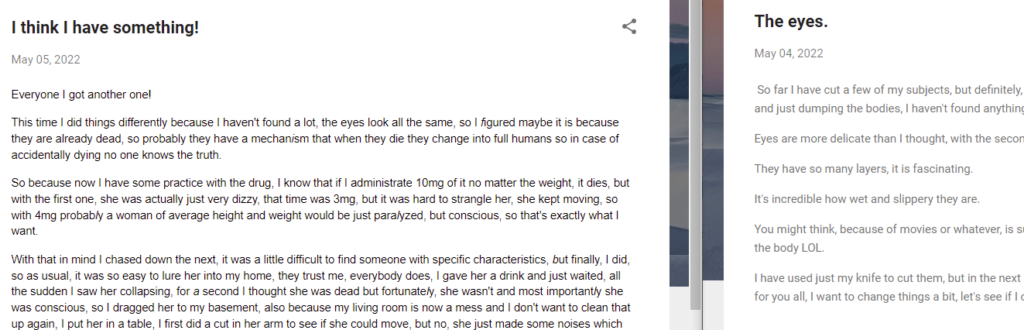
The font is different, the color is different, the size is different. Everything is different. This usually happens when a text is copied and pasted from a different source, like from a Word document or from an email and the format is kept.
My first thought, before I even started reading the text, was to only read the first word of each line, but that only resulted in nonsense and the lines do not vary in length, so that was pretty unpromising anyways. I went ahead by reading the text carefully and noticed some italic characters, namely in this part: “probably a woman of average height and weight would be just paralyzed”, which made me think the text in between those two Ls would be important, but I quickly found some more of these characters.
Instead of spotting them manually, I inspected the HTML of the page and wrote a script to output the letters.
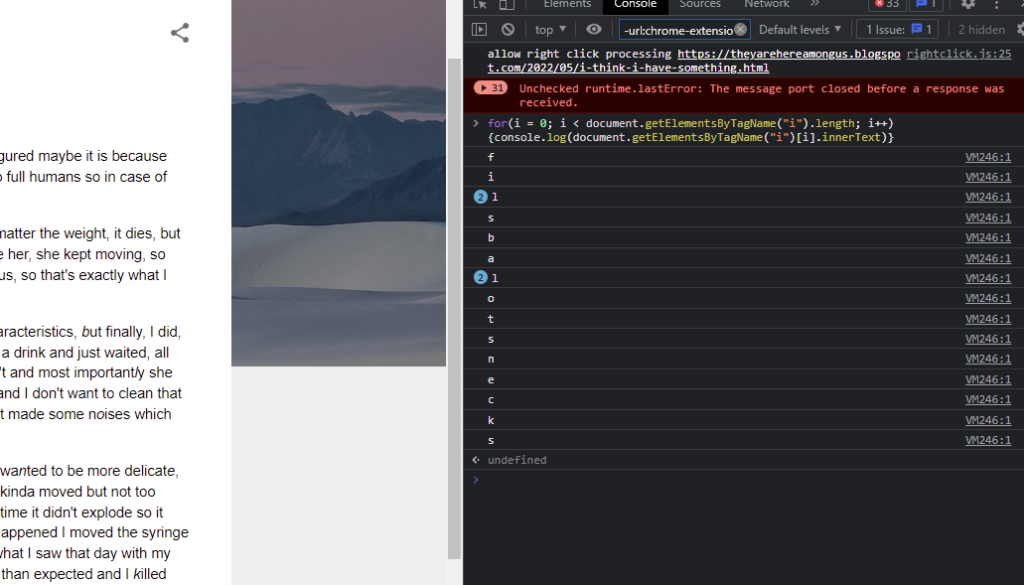
There were 17 letters: fillsballotsnecks
I noticed I could read parts of this letter sequence, but assumed it was a cipher, so I let CyberChef take a look at it, assuming it might be a Caesar cipher or something similar, but neither the Magic function nor any rotation key revealed anything, so I started thinking that the 17 letters might just be what they appear to be: Three words. But googling them did not result in anything either.
However, I did know I was looking for a location, so I did what’s called a pro-gamer move and googled “location three words” and found this neat website I have actually seen in another CTF before but didn’t think about: https://what3words.com/
Entering our three words: https://what3words.com/fills.ballots.necks shows a place called Laramie Park, which is located in Skokie, Illinois, right next to Chicago, confirming it’s the location we are looking for.
Answer: Laramie Park in Skokie, Illinois
Step 5
Alright so big hit today! There was a note found at the local university, people got suspicious at the request stated on this note and contacted the local police. The person stated on the note is not familiar at the university, the needed email address had also been cut off.
We sent the original note for forensic analysis to the lab, this will however take several days. Attached below you find a typed out copy of the note as found in the university.
Objective: Trick this person into scheduling a meeting with an undercover agent.

Step 5 took me several days and I got some involuntary hints by reading the Hacktoria discord.
I obviously started by googling for “Marlene Esther-Obdam”, but didn’t find any person who seemed like the murderer we are looking for. Then I googled for parts of the text itself like “participants for eye study” and “Chicago master degree”, but none of that resulted in anything either. Thinking about it, the CTF was only created a few days earlier and the organizers would also not want to risk we contact any random real person, so I assumed the information could not be googled, but had to be found through other means.
What kept me busy for a long time was the way the text was presented: If someone left a note somewhere, I would expect to be given either an exact photograph of the note including colors and fonts, or a text in text form. However, we are given a text as an image, which made me think it had to do with that. My first thought, again, was to only read the first word of each line or to only read every second word, but the text made way too much sense to be a code or to hide a second meaning. So I looked at the image itself, using some Steganography and image analyzing tools, looking for small details between the lines, but none of them revealed anything. Thematically, it also wouldn’t make sense to have something hidden in an artifact that is given to us by colleagues.
Then I went back to looking for “that person” by going through the YouTube channel and blog page again. The only information I got from there was that the person probably has a Gmail address because both YouTube and blogger are Google products. Issuing a password reset for the blog confirmed as much: https://www.blogger.com/forgot.g
However, it’s worth noting that Google implemented some privacy security features that prevent getting any real information about a person, especially no email address. So unless the person made a mistake or voluntarily revealed their address, it should not be retrievable through either the YouTube channel or the blog page.
Another idea I had was to message the disposable email addresses mentioned in the police report (https://hacktoria.com/wp-content/uploads/2022/05/police-reports.pdf), but those are only valid for about two hours after creation.
The final idea I had was to just look for other social media accounts with a similar name or content created recently. There is a neat little tool to automate this: https://github.com/sherlock-project/sherlock I started with “marleneestherobdam” and “aliencatcher” and then tried any combination using more or fewer words and different orders.
I did find a result for “marleneestherobdam”, but that account was created some years ago, was on a pretty random webpage, and did not show an email address.
“marleneesther” and “aliencatcher” resulted in many accounts on various platforms. I only checked those that made some sense, like Twitter, Facebook, and Instagram, and none of them seemed to belong to the murderer.
For “marleneobdam” I found just this one result.
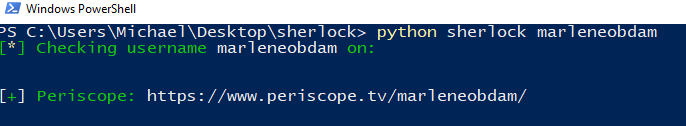
Note: Periscope redirects to Twitter, so the account really is: https://twitter.com/MarleneObdam
The Twitter account links back to the Hacktoria website, confirming it’s the correct account. It also includes an email address: mrwhiskers1260@gmail.com
So I contacted that email address, stating I wanted to participate in her study and scheduling a meeting. The answer came back a day later, including a code.
Answer: GG-WP-MUCHOSINT
Step 6
After looking at CCTV footage, we have identified the killer to be Kaylee Ann Taylor, a 41 year old DevOps engineer at the university. Local police raided her residence, but found nobody there except her pets. Speaking to her neighbors, it turns out she left town and asked them to take care of her home for a while. So far we are investigating the house and surrounding area. Local police has taken a laptop that was left behind, this device contained a lot of files that are being looked into. However, one file on the desktop immediately stood out. So far our Red Team has not brute-forced it yet, perhaps you can have a crack at it using your knowledge of the subject? In the meantime, we’ll be checking for credit card payments, cellphone calls and local traffic cameras’. BOLO went out already and all Chicago news outlets will plaster her face on every screen possible.
Find out where Kaylee Ann Taylor is hidding.
Download the file:
https://www.dropbox.com/sh/u581lvzm2klzisw/AABd6y5KjJ2Sz53tU6mXHuD7a
I couldn’t solve step 6 despite trying for some weeks during which I stopped trying multiple times but was encouraged to give it another try by other players again and again. Thank you!
Here are my thoughts on this last step.
We are given a password-protected zip archive including a jpg file called “flight-ticket”, which makes it pretty obvious what we need to try. My first idea was obviously to ask John the Ripper to open it using Rockyou, but he failed. The task briefing clearly states we should not just brute-force the password, but instead guess it based on what we know about the subject.
On her Twitter account, she posted something about her cats, including their names. Since this is the last step and we have not used that information yet, it is safe to assume the names are part of the password. So I used Wordlister (https://github.com/4n4nk3/Wordlister) to create about 500 MB worth of different combinations of the names of the cats and other keywords surrounding the subject like “Marly”, “Marlin”, “Alien” and some more and including variations like leetspeak. I used that list of words as the dictionary for John the Ripper, but again, it failed.
After many days I tried longer but simpler words. So instead of limiting the password candidates to 6 words and a maxlength of 30 characters while including variations of leet, cap, and up, I now only included the cap variation and increased the words to 10 and the maxlength to 60.
Before, I had mostly candidates like:
MR5M15T3RFluffyMR5 M1TT3N5
MRSMISTERFluffyMRS MITTENS
MRSMISTERFluffyMITTENS
MR5M15T3RFluffyM1TT3N5
MR5M15T3RFluffyMr5 m1tt3n5
MRSMISTERFluffyMrs mittens
MRSMISTERFluffyCaptain
MR5M15T3RFluffyC4pt41n
MR5M15T3RFluffyC4pt41n fluffy
MRSMISTERFluffyCaptain fluffy
MR5M15T3RFluffyC4PT41N FLUFFY
Now my candidates looked like this:
FluffyMister1260Mister BootsBootsMrs mittensMittens
FluffyMister1260Mister BootsBootsMrs mittensCaptain
FluffyMister1260Mister BootsBootsMrs mittensCaptain fluffy
FluffyMister1260Mister BootsBootsMrs mittensMrs
FluffyMister1260Mister BootsBootsMrs mittensCaptain Fluffy
FluffyMister1260Mister BootsCaptain FluffyMittensCaptain
FluffyMister1260Mister BootsCaptain FluffyMittensMrs Mittens
FluffyMister1260Mister BootsCaptain FluffyMittensMrs
FluffyMister1260Mister BootsCaptain FluffyMittensBoots
FluffyMister1260Mister BootsCaptain FluffyMittensMrs mittens
Then John finally found it, and it was so simple…
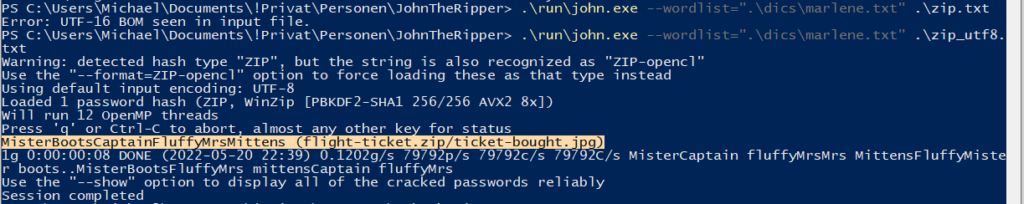
So I opened the zip archive using the password “MisterBootsCaptainFluffyMrsMittens” and got to see her flight ticket.
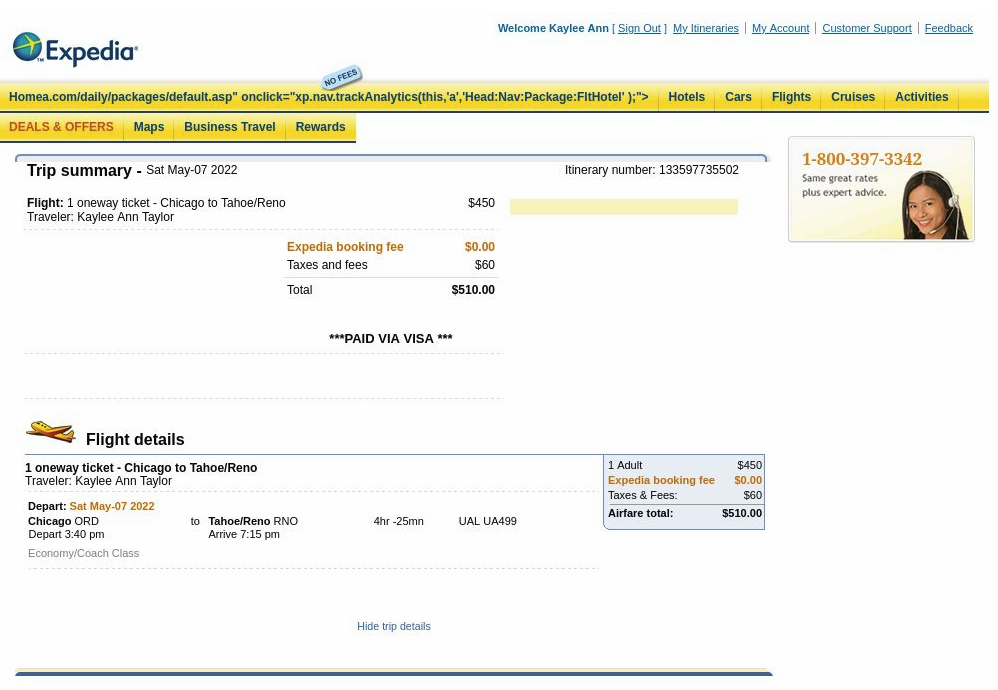
Apparently, she flew to Tahoe/Reno, which is an airport in Nevada. Since I knew her email address, I used Google Hangouts to find her OID, which is 105442598824696958229. Then I used that to find out if she made a review on Google Maps: https://www.google.com/maps/contrib/105442598824696958229/reviews/
Imagine she would review and confirm her stay at the airport. That would be funny. But she didn’t. Investigating the itinerary number didn’t reveal anything to me while investigating the flight number “UAL499” revealed that this plane actually flies from Dallas to Newark: https://flightaware.com/live/flight/UAL499/history However, the organizers of the CTF mentioned on their Discord that this is not relevant to the CTF and that we should focus on the given destination on the ticket itself.
While the ticket may not include any more information, the murderer did post some hints on Twitter: She is at a hot location in some kind of box that has solar panels. There is some kind of manager and she manages to fix some kind of air conditioner herself. She also posted this image:

I tried to find this location before I knew where she flew already, but couldn’t find it. Judging by the theme of the CTF, I assumed she would either be in Egypt or somewhere near Area 51. Area 51 actually is in Nevada, too.
But I started by using Google Lens on the image and adding “Nevada” as a search term, which revealed a pretty funny similar image.
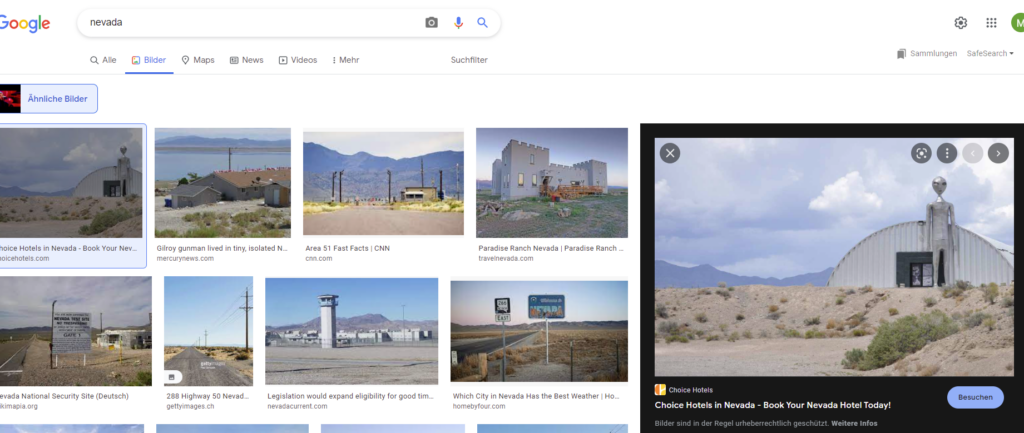
A hotel would fit her complaints about a manager, and that figure in front of the building looks like an alien, which can’t be just a coincidence, can it? Time to find the hotel… Looking for that building, I found out it’s actually an “Alien Research Center” on the “Extraterrestrial Highway”. Going along that Highway on Google Street View, I saw many things that looked similar to the image on Twitter, but no match. Hotels and other points of interest also didn’t seem to have the characteristics shown in the image nearby.
One hotel that looked very promising was the “Little A’Le’Inn”. It’s alien-themed as the name suggests and it has a storage container nearby that would fit the description of a “box”. Also, a hint given by the CTF staff was that the solution would make us laugh, so it is probably not some random hotel like every other. But even though this inn seemed like a perfect match, I couldn’t find the characteristics seen in the image.
The storage container looks like this:

Another box that can be seen from the Alien Research Center, which I think is a gift shop:

But in the end, I couldn’t locate her exactly, because I just couldn’t find the exact view she posted on Twitter.
So there you have it, I let her escape!
This CTF was much fun, especially since I was really invested in it because it was live and no write-ups or hints were available at the beginning even if I wanted to look for them. I really liked how unambiguous the answers have been: When I found them, I always knew exactly that I was correct about them without any doubts.
Also, I enjoyed reading the story. I’ve never heard of using heterochromia in a story like that, and making that into an alien-killer story made perfect sense!
Looking forward to next month’s CTF!
If you want to read other peoples’ write-ups, check them out here: https://hacktoria.com/write-ups/
1 thought on “Hacktoria | Downtown Murderer CTF – Wripte-Up”