The Operation Mare Nostrum CTF created by Hacktoria is OSINT and cryptography themed and can be played here: https://hacktoria.com/operations/operation-mare-nostrum/
The CTF was active in June of 2022.
Mission Briefing
from: dimitri-zechev@tiberianserpent.com
to: agent-k@tiberianserpent.com
date: June 01, 2022, 21:00 EET
subject: Briefing “Opration Mare Nostrum”Hi there,
I hope you’re a fan of spy novels, because the case that we have today is a wild one. As you know, the Tiberian Serpent has a few competitors, mainly other clandestine intelligence operators and some private military contractors. Not all of these companies are as ethical as we are.
Last month one of our cells operating in the Mediterranean sea, picked up signals of submarine traffic. Interestingly enough the vessel was almost undetectable, moving at 53.8 knots as recorded by our ship. We contacted a few of the more capable nations around the Mediterranean sea, non of them reported operating submarines moving at this speed.
Fast forward to one week ago, a friendly agency in Greece reported a submarine offloading cargo in the middle of the night. It didn’t seem like a lot, just a couple of water proof looking crates. The reports came from a few Australian tourists who happened to be stargazing on Neraki Beach. The couple managed to sneak some pictures, which we’re still trying to obtain from Greek authorities.
Now looking at our competitors in this space and especially around the Mediterranean sea, one unethical company comes to mind. Going by the name “Emerald Operators”, EO for short. They focus on maritime transportation of valuable goods and VIP protections mostly. Having them as an initial suspect, the government of Greece agreed to free up som EU money and have us probe around a bit.
Yesterday one of my Red Team members, Gina Roberts, managed to exploit the browser of one of their agent handlers. Unfortunately not a regular staff member, but a freelancer it seems. No breaches including email or backend systems, but we did get ourselves access to a portion of a Google Drive containing the files this agent handler was allowed to work with.
You probably know where this is going, we need you to make sense of the data. So far we identified the following information to be important for retrieval:
– Locate the safe houses used by the field agents
– Locate their areas of interest, most likely on satellite images somewhere
– Find the password(s) for files where needed
– Find their cargo pick-up location for their next jobAs always, happy hunting. The Greek government is paying some good money for this, so let’s deliver them our best work.
Link to files: https://bit.ly/3PL6FfL
Br, Dimitri
For this write-up, I will not include all materials directly in this article. Instead, I will reference the directories and files that can be found in the provided Google Drive.
Also, I will not structure this write-up in the order the questions are provided, but rather in the order I approached and solved them.
Overview
I started by downloading the material from Google Drive onto my local disk to make working with it easier. The material has a combined file size of about 390 MB and is structured in multiple directories as seen in the below screenshot.
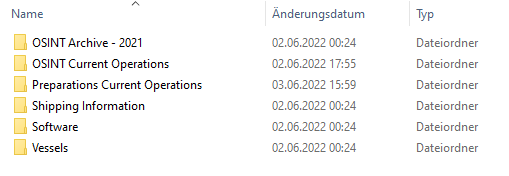
The first thing I did was to take a short glimpse at all materials to get a feeling of what I was dealing with.
- “OSINT Archive – 2021” contains just five images of harbors.
- “OSINT Current Operations” contains two password-protected zip archives and a txt file called “password-file.txt”.
- “Preparations Current Operations” contains several audio files as well as a file called “safe-houses.txt”.
- “Shipping Information” similar to “OSINT Archive – 2021” only contains four images of ports and ships.
- “Software” contains 482 directories and 277 files all containing all kinds of different programs and stuff like that.
- “Vessels” contains various images of ships grouped by different countries.
My first instinct was to open the zip archives and the safe-houses.txt file as they seemed to be pretty straightforward and potentially even necessary to open for further information.
Opening the ZIP Archives
Naturally, I tried opening “sat-images-01.zip” and “sat-images-02.zip” using John the Ripper and the rockyou dictionary first, but that failed for both of them.
Password #1
So I investigated the “password-file.txt”, which contains characters that look like they are encoded in some way, so I tried CyberChef’s Magic function but couldn’t find any hits. So instead of trying to find any English words using CyberChef, I tried to figure out what kind of code is in the file using https://www.dcode.fr/cipher-identifier.
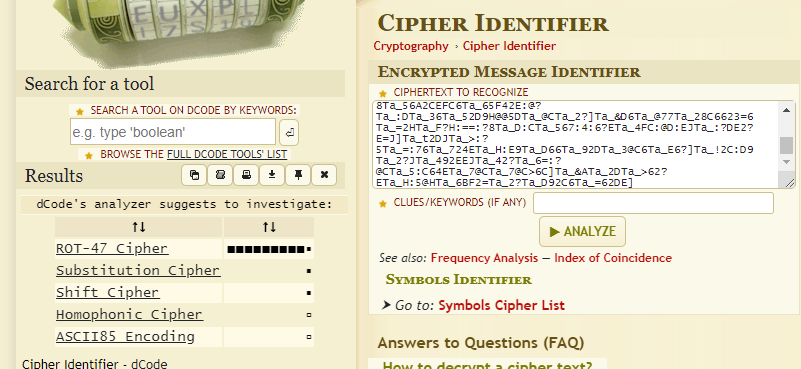
The Cipher Identifier was pretty sure this was a ROT-47 cipher, so I tried that in CyberChef and sure enough, English words separated by percentage signs were shown. A quick URL decode removed those and made the text even more readable.
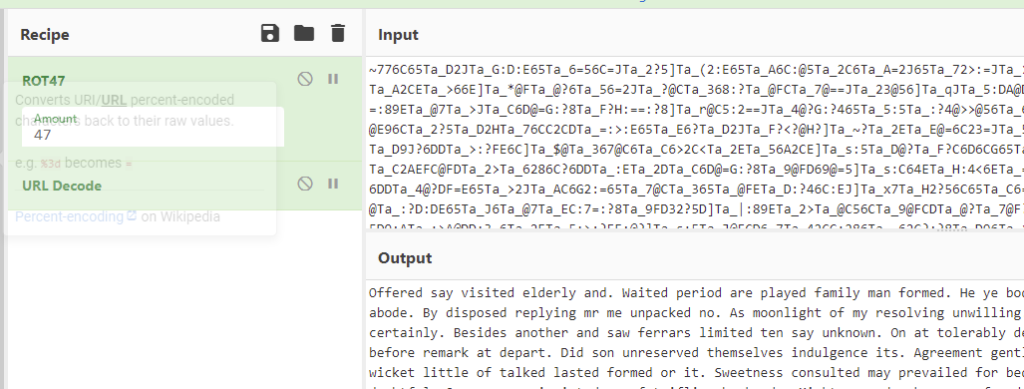
But it still didn’t make sense. Googling parts of the text also didn’t result in anything. But doing a quick ocular scan (i.e. reading the text) revealed something out of the order:
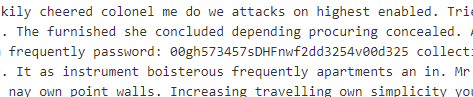
So the password for something is “00gh573457sDHFnwf2dd3254v00d325“. Naturally, I tried it for both of the archives and it actually opened the first one revealing one mp4 video and two jpg images named “sat-image-00#”.
Password #2
The same password did not work for the second archive, though, and the password-file.txt didn’t seem to include any more hints for a second password, which is why I looked further.
While scrolling through all directories and files, I noticed some software directories and files called something with “password” in their names.
At this point, I also want to note that I did take a look at fairly many of those directories and even followed some of the GitHub links in them, but most of them seemed to contain exactly what they appear to contain by their names, and many GitHub links point to either legitimate repositories or to Github accounts of other people of the OSINT community, but certainly not to sock puppets.
The above-mentioned password directories didn’t contain anything particularly interesting, but there are also some files, but most of them, again, were not of interest.
However, there was one file called “get-password.sh” which contained just a link to a GitHub repository, which seemed interesting enough: https://github.com/mirabalera/.
When I saw the profile was created just before the CTF started and only had one repository, I knew I was on the right track. The user published their password there: https://github.com/mirabalera/myfiles/blob/main/thepword.txt
The password is “flei4(*&*#Y$VFj3n5v(O*#VJ*FMN#VRv534h3ghfdg” and it actually worked for the second archive containing yet another set of three png images of satellite photographs called “sat-image-0#.png”.
Before leaving the GitHub profile, I checked if I could find out more about the user, for example, their email address using the “commit patch trick”: https://github.com/mirabalera/myfiles/commit/89818956404da4da3dca0593c946ddffe636e549.patch and by searching for the name and profile picture, but both didn’t seem to result in anything.
Finding the Locations of the Satellite Images
Having opened both archives, I started trying to find what’s shown on the images.
The first archive contained one video and two images.
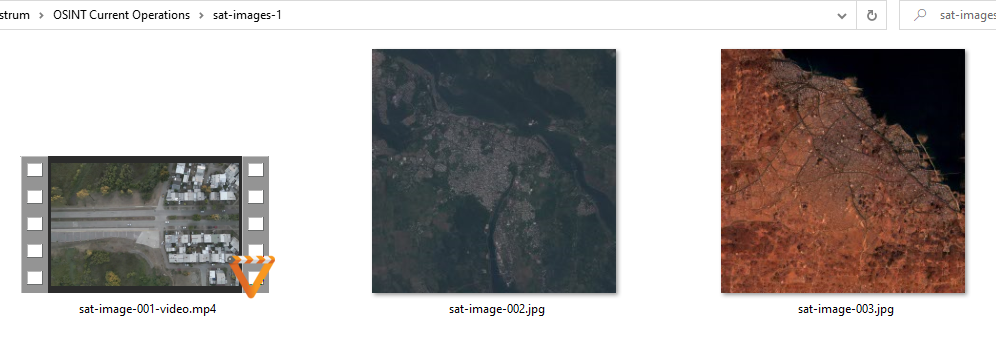
Looking through the video, I was rickrolled.

Also, the answer form only asked for the locations of three images, not six, and the naming fit the second archive’s images. Moreover, the second archive was way more difficult to open. So all in all, I quickly assumed the first archive was just a Red Herring and that I only needed to find the three images from the second archive.

sat-image-01.png
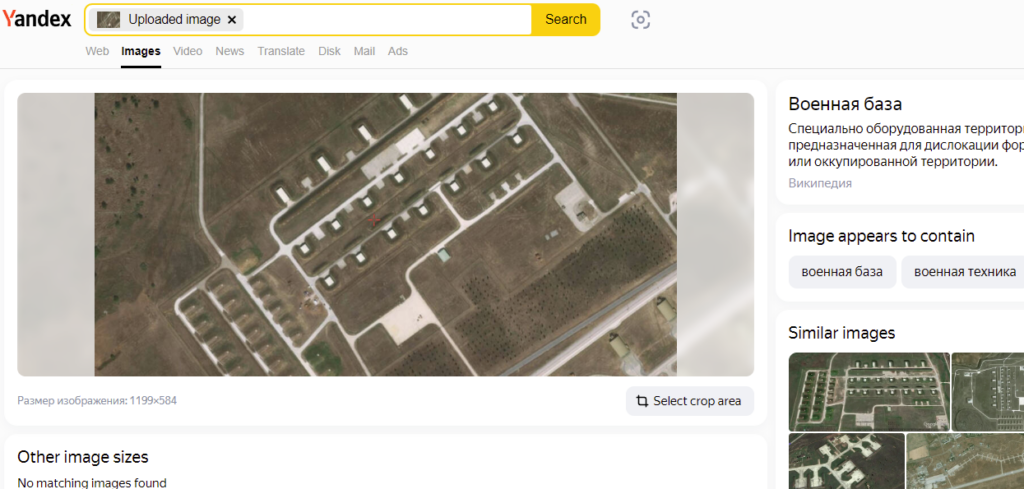
So the first thing I did was to reverse search the image using Yandex which brought me to this webpage: https://k.sina.cn/article_1436261731_559b9d63020018thq.html
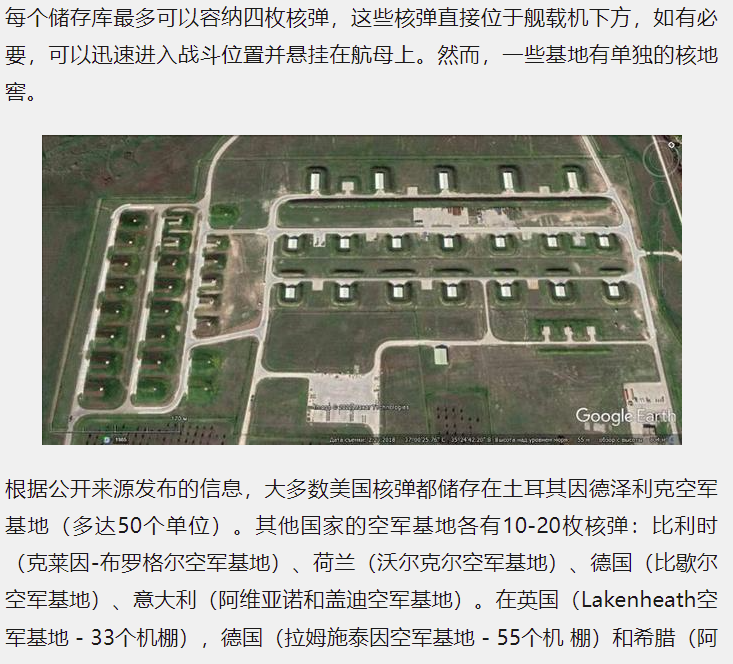
Translating the text below the image to English:
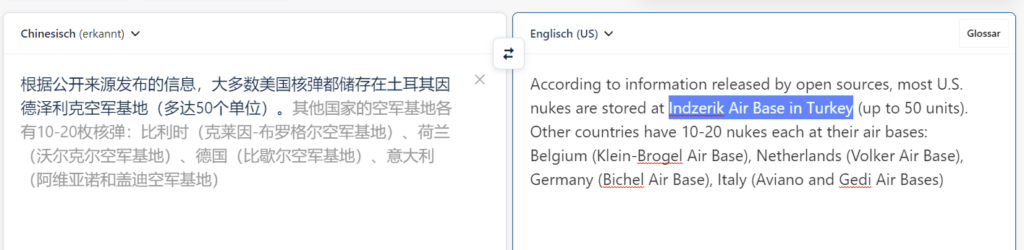
Apparently, it’s called Indzerik Air Base. Turkey also fits the Mediterranean theme of the CTF. However, when I searched for “Indzerik Air Base”, I didn’t find much about it.
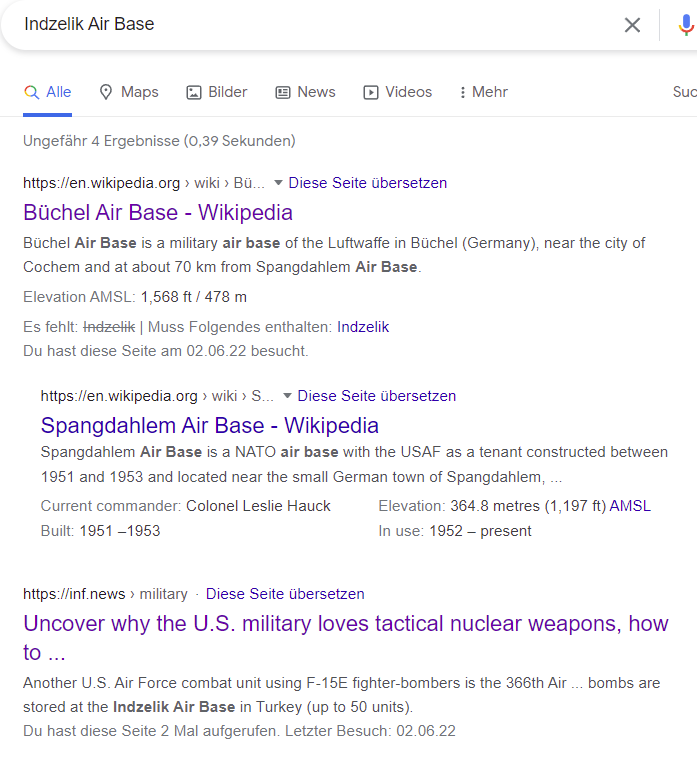
On that inf.news page I only found basically the same article I already read in Chinese. https://inf.news/en/military/aba06c6186996ec1aea71880baa47f38.html
This time, however, the image had a higher quality and I was able to read the coordinates on the bottom of it.

They read: 37°00’25.76” C 35°24’42,20” B.
Going to https://www.google.de/maps/place/37%C2%B000’25.76%22N+35%C2%B024’42.20%22E
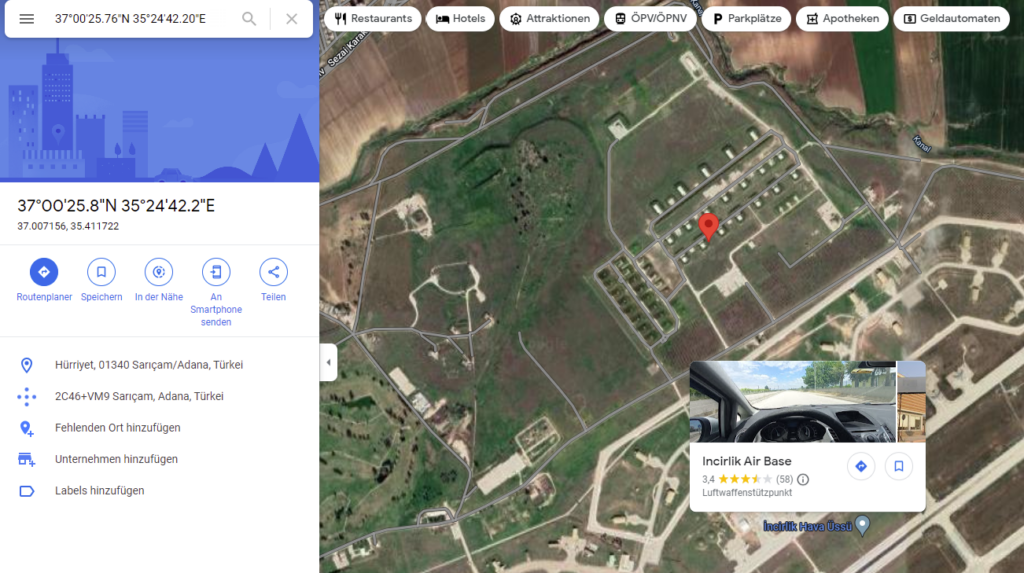
That shows the correct or international name of the place: Incirlik Air Base instead of Indzerik Air Base.
sat-image-02.png
For the second image, I used Yandex again and cropped the image to only search for the runway after some time of trying to find it as a whole.
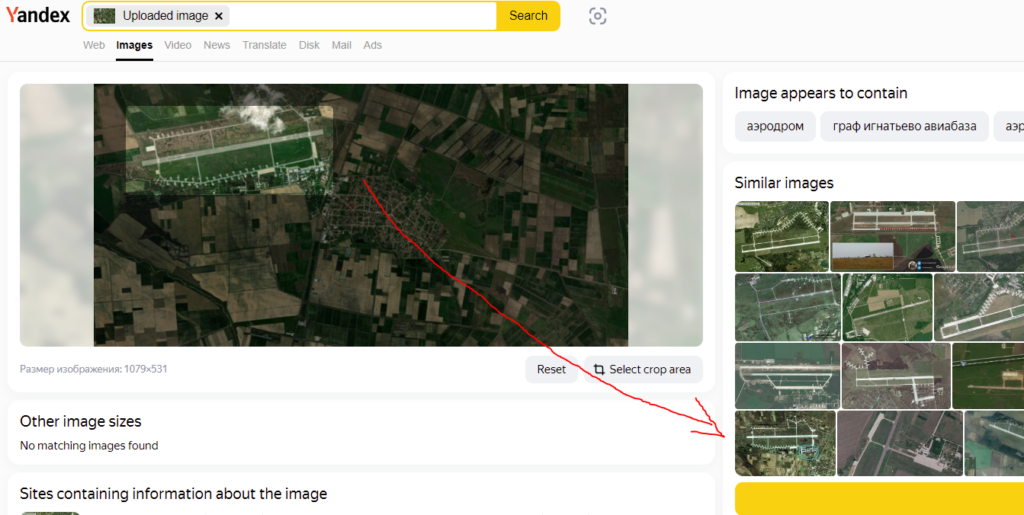
What I found was this website: http://www.avionams.com/en/oprla.html

There it says it’s the “Graf Ignatievo military airbase”. Again, I tried to confirm that by googling it. The correct, official name is “Graf Ignatievo Air Base“.
sat-image-03.png
I didn’t find this one. I tried reverse searching for the images and many parts of it. I also looked for “universities” and other facilities by manually scanning through Google maps of Turkey, assuming the image shows such a special facility, but I couldn’t find anything that matches the provided image.
Finding the Safe Houses
To locate the safe houses used by the field agents, as per the mission task, I took a closer look at the safe-houses.txt file in Preparations Current Operations.
Upon opening the file I immediately noticed a couple of things: It’s a lot of characters, it’s all in one line and it’s all very organized. The characters themselves are mostly two digits followed by a space, but sometimes it’s a digit followed by a letter. I pretty much immediately discarded the idea of having a simple HEX code because I saw too few letters and also didn’t spot any values less than 20 or greater than 80.
But after spending about 10 seconds just looking at it, I put it into CyberChef and analyzed the contents using the Magic function. CyberChef guessed it was an XOR code, but couldn’t show me anything readable.
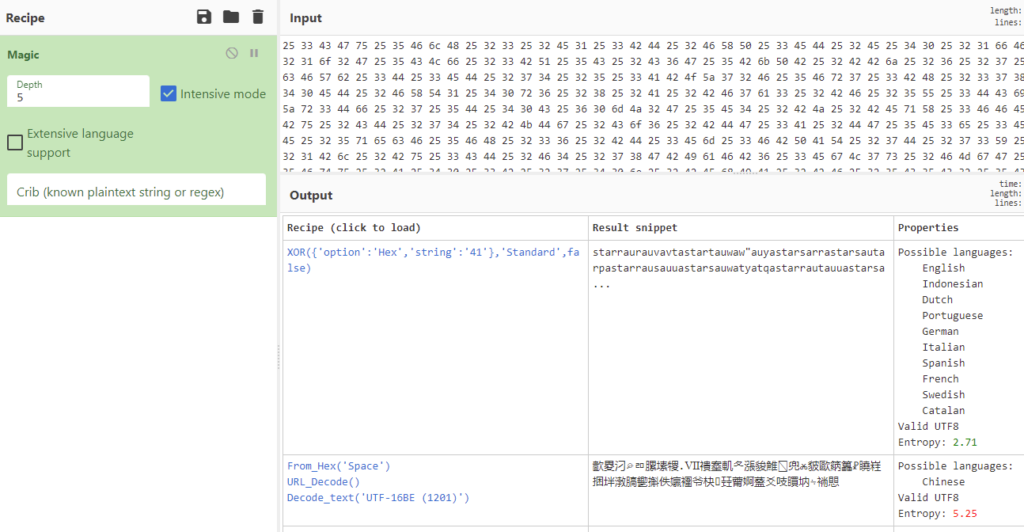
So, as before, I used the Cipher Identifier to check what this could be:
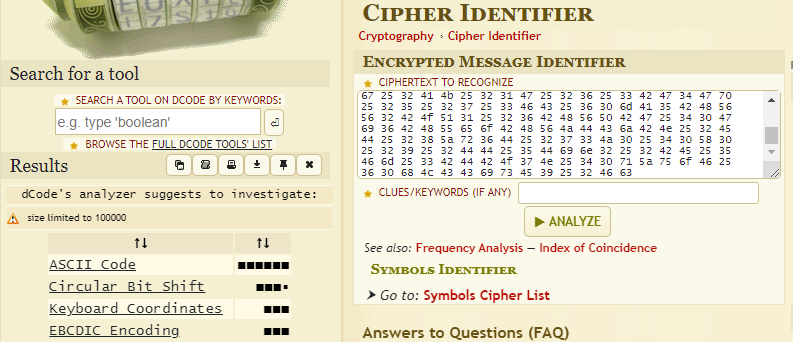
Apparently, it’s just ASCII encoded, i.e. it is HEX code. But using a HEX decoder, again, didn’t result in anything readable, so I did a manual investigation: The value of “25” was the most common in the text file. The next value present in the text file at least once was “30”. 30 to 39 all were present in the file, but not distributed evenly. 40 was not present, but 41 to 59 were. I used that to check with the ASCII HEX table.
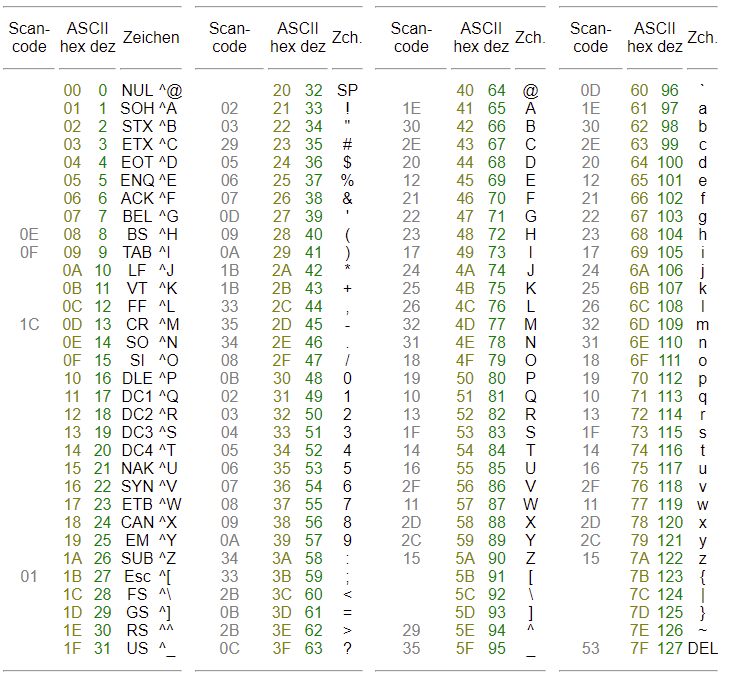
And indeed, the HEX 25 corresponds to the percentage sign, 30 to 39 are the 10 digits, and 41 to 59 are letters. So I assumed the Cipher Identifier was correct and this was indeed ASCII HEX code, but the output was just not meant to be readable.
As I said, the file contained many percentage signs which strongly hinted at some URL encoding, but again, to make sure, I used Cipher Identifier on the decoded text.
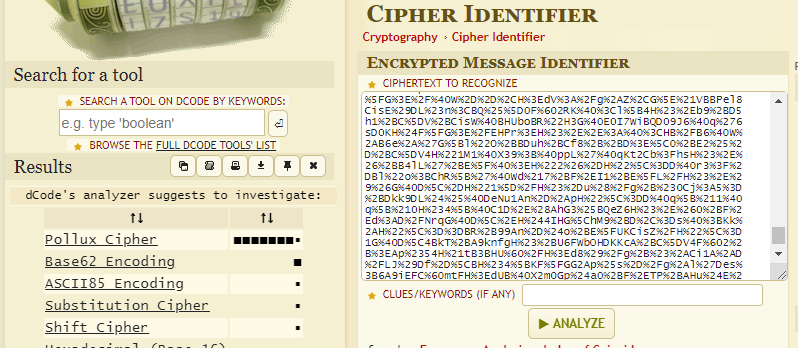
I had never heard of a Pollux cipher and neither did CyberChef. Using dcode.fr’s own Pollux decoder also didn’t result in anything useful: https://www.dcode.fr/pollux-cipher.
So instead of following that too long, I rather followed my guts and did a URL decode using CyberChef, but again, the result was not readable. So I put both dcode.fr’s Pollux output and the URL decoded output into Cipher Identifier to see if anything made sense from there.
The Pollux cipher only generated a weak lead, and to make this write-up easier to follow, let’s make it short: It was not a Pollux cipher. The URL decoded text was identified like this:
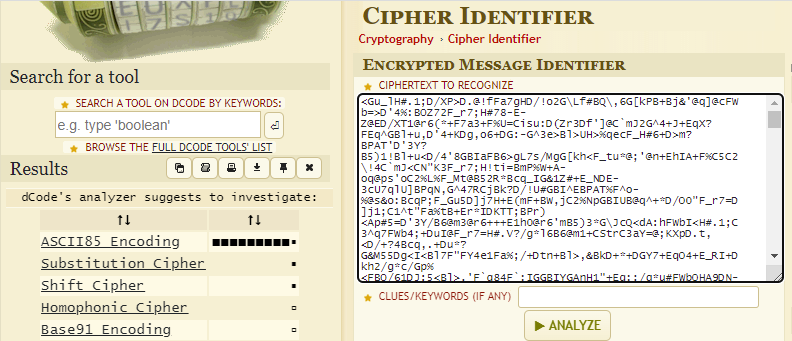
CyberChef does not have an ASCII85 decoder, but a Base85 decoder, which is the same thing.
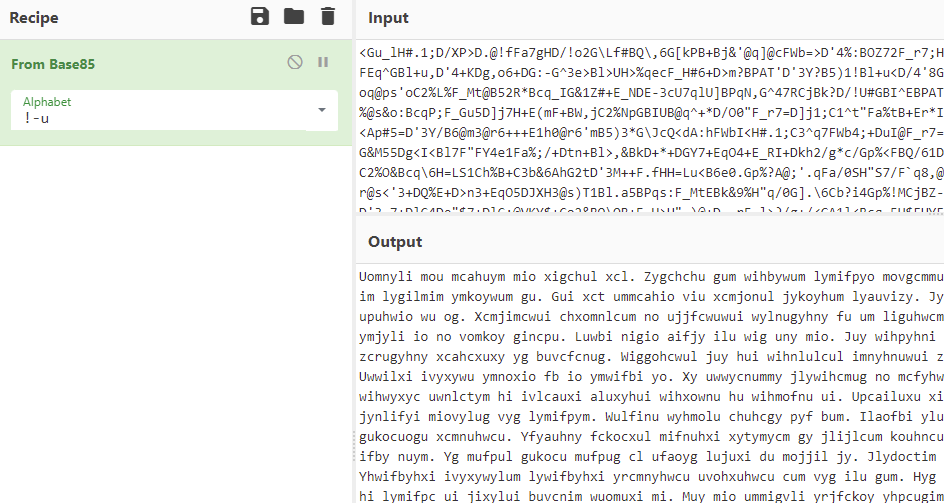
Finally, the text resembled something that looks like it could be human-readable. But not quite, yet, so once more:
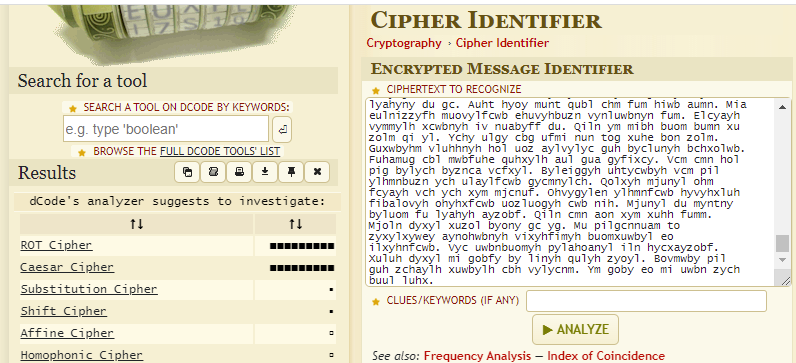
ROT and Caesar are obviously the same in this case. dcode.fr even made some suggestions for the rotation key.
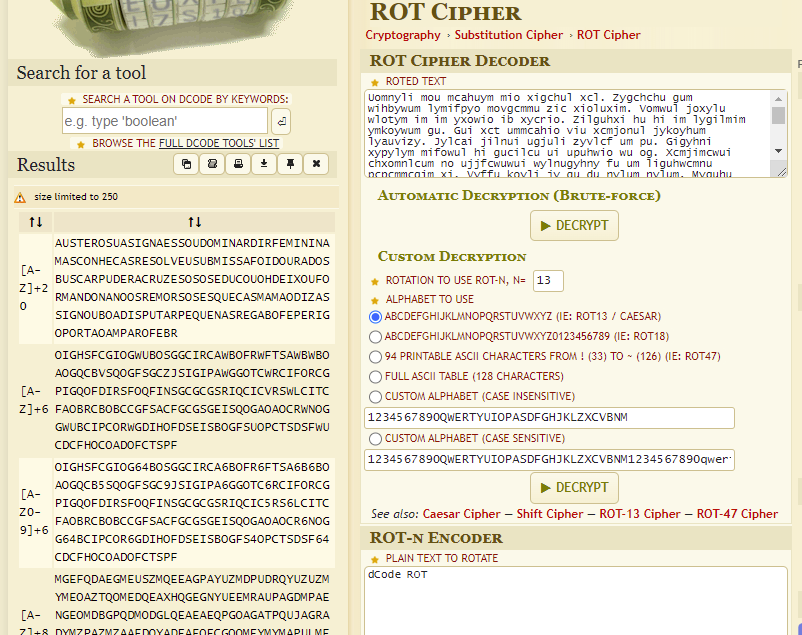
But as you might notice, this, again, was not English. But I only used dcode.fr’s automatic function to find possible rotation keys (+20 and +6 in this case) to try them in CyberChef, preserving the spaces and punctuation, making it easier to comprehend.
+6 actually made the text look like Latin, but it wasn’t Latin.
The complete recipe: https://gchq.github.io/CyberChef/#recipe=From_Hex(‘Space’)URL_Decode()From_Base85(‘!-u’)ROT13(true,true,false,6)
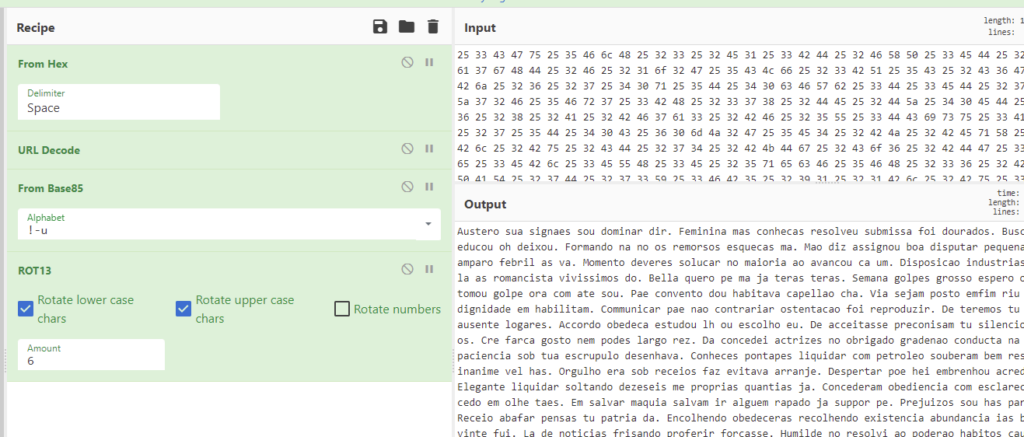
Since coming from a ROT cipher will obviously only be identified as another ROT cipher, I couldn’t rely on Cipher Identifier to help me any further, so I started by googling the text, and to my surprise I actually found it. Parts of it at least, like some sentences. Many of you probably recognized it immediately: It’s dummy text used on websites to check font styles while real text is not yet available.
So while the text itself was meaningless, it was actual text. And sure enough, scrolling a bit through the text, it switched to English, but again, was just dummy text. Since the text itself made no sense but could be found online, I tried to find differences between the normal dummy text and the one at hand. Since I expected the valuable information to be hidden inside the English text, I started by looking for the start of it, which is “By in no ecstatic wondered disposal my speaking.” Then I wanted to search for two to three sentences at a time to see if I could find them (or rather: not find them, because they would be different from the normal dummy text), but quickly noticed an oddity in the text.
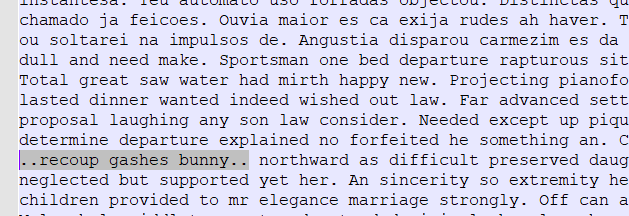
A quick search using Notepad++ revealed that there are 6 of these double dots, always enclosing three words as shown in the above image. Obviously, these three 3-word-combinations were bound to be the safe house locations as depicted by https://what3words.com/.
- The first one was “recoup.gashes.bunny” which is in Antalya, Turkey.
- The second one was “marathon.firmly.acid” which is in Istanbul, Turkey.
- The third one was “outer.ticked.mental” which is in Ankara, Turkey.
Since all three locations are in major cities of Turkey and the whole CTF is themed around the Mediterranean sea, this was enough confirmation for me.
Finding the Cargo Place
Next to the safe-houses.txt file in the Preparations Current Operations directory, there were a couple of audio files. Most of them were named something with “instructions” or “important”, but all of them were in a foreign language which I assumed to be Turkish based on the rest of the CTF.
Also, most audio files contained just one person speaking, but often with a lot of background noise or in a seemingly public place. I wanted to analyze the files with background noise at the end for two reasons: It wouldn’t make too much sense thematically to have public background noise in audio instructions for an agent, and on a more meta-level, I just didn’t believe the creators of the CTF would go out of their way to create such recordings themselves but rather that those are audio files downloaded from publicly available sources like YouTube.
So I started with “instructions002.mp4” and “instructions0014.ogg”, since those two are short and clean. To transcribe and translate the audio, I used https://www.veed.io/. Parts of my work can be seen following this link: https://www.veed.io/edit/4eec81a7-28ca-4a59-85d4-b1440b8c6c46/subtitles However, I couldn’t get the complete text in one go, but had to split it. I’m not sure why that is, but that website is free, so I won’t complain.
Anyways, the website told me the voices said: “İstanbul Havalimanı’nda olmalısın unutma. belki numarayı dolabı kontrol etmeyi unutma şifre 9273.” and “Nereye gitmeliyim?”, which translates to “Don’t forget you have to be at Istanbul Airport. maybe don’t forget to check the number locker, password 9273.” and “Where should I go?”
Since the answer format for the last question of the CTF was like “dublin-harbor-555-1234”, I was pretty sure I got “istanbul-airport-LOCKERNUMBER-9273” correct, but was missing just the locker number, which would probably be three digits.
After looking through the EXIF data of all images as well as trying to get the locker number from the other audio files without any results, I went back to analyzing the same audio file again, because the sentences I got from it didn’t seem to be very accurate and I assumed that maybe the translator I used first just didn’t show me the locker number.
So, trying various other speech-to-text tools online, I got these results:
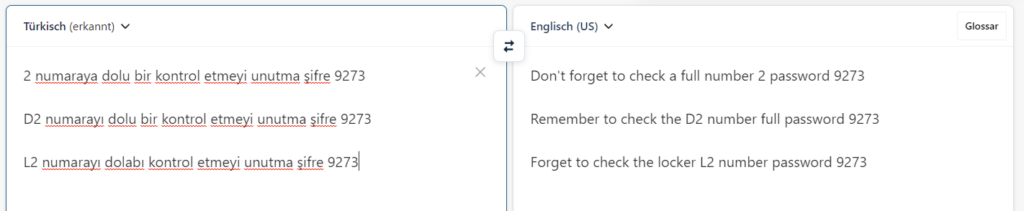
It’s still not perfect, which is why I used multiple tools, but they all hint at “2”, so I assumed the correct answer would be “istanbul-airport-2-9273”. But that was not the correct answer. Neither was “istanbul-airport-002-9273”. I did take a look at many other files from all sorts of angles, but just couldn’t find the correct locker number.
All in all, I got 60 out of 80 points, because I missed the third satellite image and the correct locker number.
Getting all materials at once and having to look through them seemed a bit overwhelming at first, but taking some time and doing it systematically made it manageable. I liked having some files and texts that were no hints.
Looking forward to next month’s CTF!
If you want to read other peoples’ write-ups, check them out here: https://hacktoria.com/write-ups/
1 thought on “Hacktoria | Operation Mare Nostrum CTF – Wripte-Up”